- For 802.11 wireless LANs, which of the following is a feature shared by both WPA2-PSK and WPA2-Enterprise?
(a) Both utilise server-side authentication using server-side certs
(b) Both support 128-bit AES-CCMP
(c) Both support WPS (Wi-Fi Protected Setup)
(d) Both use RC4 to provide integrity for data frames
(e) Both can only be used in the 2.4 GHz frequency ranges
Answer:
(b)
Explanation:
(a) is a possibility for WPA2-Enterprise only, depending on implementation
(c) WPS is supported only for PSK
(d) RC4 is an encryption algorithm (i.e. confidentiality not integrity) – it was used by WEP, but is not used in WPA or WPA2
(e) Both can be used in both ranges (2.4 & 5 GHz)
- Which of the following access control mechanisms allows information owners to control access to resources by evaluating the subject, object & the environment?
(a) Rule-based access control
(b) Attribute-based access control
(c) Role-based access control
(d) Discretionary access control
Answer:
(b)
Explanation:
Attribute-based access control allows you to create policies that control access to resources by evaluating attributes of the subject (e.g. clearance, department, role), object (e.g. type, owning department, classification/sensitivity) and/or environment (e.g. time, location).
- Your accounting dept is moving from locally-installed software to a SaaS solution provided by a large accounting software vendor. The process will involve moving existing accounting data to the SaaS provider’s cloud-based servers. Which of the following would your organisation MOST LIKELY consider before making the move? (Choose two)
(a) SLA (Service Level Agreement)
(b) MOU (Memorandum Of Understanding)
(c) NDA (Non-Disclosure Agreement)
(d) Software License
(e) ISA (Interconnection Service Agreement)
Answers:
(a), (c)
Explanation:
An SLA will define metrics for performance and uptime, and sometimes penalties to be paid by the provider in the event of an SLA breach. MOU’s are a voluntary, non-legally binding agreement between two organisations, which would not be appropriate in this case. An NDA would be required to oblige the provider not to disclose your organisation’s data. Software licenses are generally used for locally-installed software. An ISA is used when connecting the networks/resources of two organisations with differing security policies, and would generally not be required for accessing a SaaS solution e.g. via a web browser.
- Which one of the following is NOT a characteristic of the Challenge Handshake Authentication Protocol?
(a) Challenges are encrypted using a symmetric algorithm
(b) Authentication is negotiated via a 3-way handshake
(c) Authenticator will randomly require re-authentication
(d) CHAP supports mutual authentication by client & server
Answer:
(a)
Explanation:
(a) The challenges are hashed with your password (i.e. one-way encryption, not symmetric)
(b), (c) and (d) are all characteristics of CHAP. Note that the CHAP 3-way handshake (challenge, response, accept/reject) is completely different from the TCP 3-way handshake!
- Which of the following represents the BEST reason to upgrade your web application servers to TLS 1.3?
(a) The SNI is encrypted by default in TLS 1.3
(b) The server certificate is encrypted when sent to the client
(c) TLS 1.3 supports a larger number of legacy algorithms
(d) The server uses certificate pinning to speed up connection times
Answer:
(b)
Explanation:
(a) SNI (Server Name Identification) is the ability for the client to specify the name of the site they are connecting to as part of the client”hello” message. This enables the server to support multiple websites on a single IP address. ESNI (Encrypted Server Name Identification) does exist, but is not a feature of TLS 1.3, and is not yet widely supported.
(b) Prior to TLS 1.3, the server certificate was sent in plaintext, which reveals the name of the site and raises privacy concerns.
(c) TLS 1.3 drops support for a large number of less secure legacy algorithms.
(d) Certificate pinning is a feature of OCSP and is nothing to do with TLS 1.3 per se.
- Which of the following is a benefit of implementing DNSSEC?
(a) Using encryption, DNSSEC prevents service providers from mining your DNS queries
(b) DNSSEC prevents you from going to malicious websites by redirecting your connection attempts
(c) DNSSEC speeds up name resolution by compressing queries & answers
(d) DNSSEC authenticates server responses using digital signatures
Answer:
(d)
Explanation:
(a) DNSSEC does not provide confidentiality for DNS lookups.
- Which of the following differentiates DOM-based XSS attacks from reflected & stored XSS attacks?
(a) DOM-based XSS is stored on the web server and sent to a victim when visiting the web page
(b) DOM-based XSS will not be visible in the HTML source of the page
(c) DOM-based XSS relies on tricking a user into clicking on a malicious hyperlink
(d) DOM-based XSS exploits a server-side flaw, and stored & reflected XSS are client-side exploits
Answer:
(b)
Explanation:
In both reflected and stored vector attacks, scripts are sent to the victim’s browser within the actual HTML code. DOM-based XSS uses the JavaScript Document Object Model to manipulate the content of the page programmatically, and inserts the code that way.
(c) could be true for both types of XSS.
- Which of the following is a key concept that provides for the security of stream ciphers in modern cryptography systems?
(a) Digital signatures
(b) Confusion
(c) Collision resistance
(d) Diffusion
(e) Entropy
(f) Asymmetry
Answer:
(b)
Explanation:
(b) Confusion attempts to make it as difficult as possible to determine the relationship between plaintext & ciphertext. Confusion is primarily achieved through substitution, and can be applied in both stream and block ciphers.
(d) Diffusion is a mechanism that improves the security of block ciphers, and cannot be used with stream ciphers. This is primarily achieved through transposition (i.e. jumbling up the data.)
- Which of the following is true regarding the use of RAID 6?
(a) Requires a minimum of 6 drives to implement
(b) It can remain functional with two simultaneous drive failures
(c) It has a net cost of one drive to store parity data
(d) It has a faster read speed than RAID 5
Answer:
(b)
Explanation:
(a) RAID 6 can be implemented with a minimum of 4 drives
(b) RAID 6 can tolerate the failure of two drives at the same time
(c) You lose the net equivalent of two drives to parity
(d) There is no read speed difference between RAID 5 and RAID 6
- Which of the following is NOT a characteristic of tunnel-mode IPSec?
(a) Tunnel mode IPSec encrypts the entire original IP packet
(b) Tunnel mode IPSec hides the number of nodes communicating through the link
(c) Tunnel mode IPSec provides end-to-end security for client & server
(d) Tunnel mode IPSec will still allow for NIDS to provide value on the LAN side of links
Answer:
(c)
Explanation:
Transport mode can provide end-to-end security between client and server, but tunnel mode cannot. This is because the portion of traffic from the client to the IPSec VPN concentrator at one end, and from the concentrator at the other end to the server, is not IPSec-protected.
Tough Questions 121-130
- Which federal government agency has responsibility for ensuring the security of government computer systems that are not used to process sensitive and/or classified information?
(a) National Security Agency
(b) Federal Bureau of Investigation
(c) National Institute of Standards and Technology
(d) Secret Service
Answer:
(c)
Explanation:
NIST is charged with the security management of all federal computer systems not used to process sensitive national security information. The NSA (part of the DoD) is responsible for managing systems that process classified and/or sensitive info.
- Which law protects the rights of citizens to privacy by placing restrictions on the authority granted to government agencies to search private residences & facilities?
(a) Privacy Act
(b) Fourth Amendment
(c) Second Amendment
(d) Gramm-Leach-Bliley Act
Answer:
(b)
Explanation:
The Fourth Amendment of the US Constitution sets the “probable cause” standard that law enforcement officers must follow when conducting searches and/or seizures of private property. It also states that officers must obtain a warrant beforehand.
- What is the broadest category of computer systems protected by the Computer Fraud & Abuse Act, as amended?
(a) Government-owned systems
(b) Federal interest systems
(c) Systems used in interstate commerce
(d) Systems located in the United States?
Answer:
(c)
Explanation:
The original CFAA covered only systems used by the government & financial institutions. It was broadened in 1986 to include all federal interest systems. The Computer Abuse Amendments Act of 1994 further amended the CFAA to cover all systems used in interstate commerce, including a large portion (but not all) of the computer systems in the US.
- Matthew recently authored an innovative algorithm for solving a mathematical problem, and he wants to share it with the world. However, prior to publishing the software code in a technical journal, he wants to obtain some sort of intellectual property protection. Which type of protection is best suited to his needs?
(a) Copyright
(b) Trademark
(c) Patent
(d) Trade secret
Answer:
(a)
Explanation:
Copyright is the only type of protection available here. It covers only the specific software code used. It does not cover the process or ideas behind the software. Patent protection does not apply to mathematical algorithms. Matthew can’t seek trade secret protection because he plans to publish the algorithm in a public technical journal.
- What law prevents government agencies from disclosing personal information that an individual supplies to the government under protected circumstances?
(a) Privacy Act
(b) Electronic Communications Privacy Act
(c) Health Insurance Portability & Accountability Act
(d) Gramm-Leach-Bliley Act
Answer:
(a)
- Which one of the following types of licensing agreements does not require that the user acknowledge that they have read the agreement prior to executing it?
(a) Standard license agreement
(b) Shrink-wrap agreement
(c) Click-wrap agreement
(d) Verbal agreement
Answer:
(b)
Explanation:
Shrink-wrap license agreements become effective when the user opens a software package. Click-wrap agreements require the user to click a button during the installation process to accept the terms of the licence agreement. Standard licence agreements require the user to sign a written agreement prior to using the software. Verbal agreements are not normally used for software licensing, but require some active degree of participation by the software user.
- What is the standard duration of patent protection in the US?
(a) 14 years from the application date
(b) 14 years from the date the patent is granted
(c) 20 years from the application date
(d) 20 years from the date the patent is granted
Answer:
(c)
- Which one of the following is not a requirement that ISPs must satisfy in order to gain protection under the “transitory activities” clause of the DMCA?
(a) The ISP and originator of the message must be located in different countries
(b) The transmission, routing, provision of connections or copying must be carried out by an automated technical process without selection of material by the service provider
(c) Any intermediate copies must not ordinarily be accessible to anyone other than anticipated recipients and must not be retained for longer than reasonably necessary
(d) The transmission must be originated by a person other than the provider
Answer:
(a)
Explanation:
The DMCA does not include any geographical location requirements for protection under the “transitory activities” exemption. The other options are three of the five mandatory requirments. The other two requirements are that the ISP must not determine the recipients of the material, and the material must be transmitted with no modification to its content.
- Which of the following is NOT a benefit of using an FHRP (First Hop Redundancy Protocol) in your network routing infrastructure?
(a) Hosts always have at least two gateway IP addresses that provide fault tolerance
(b) Routers share a virtual IP address, allowing either one to use the address
(c) A standby router provides failover support to the active router
(d) An active router can be manually preempted for hardware maintenance tasks
Answer
(a)
Explanation:
FHRP is a way to help create highly-available networks, by taking two or more routers and creating a virtual router. That virtual router will have an IP address, and one of the nodes (the “active” nodes) will respond to requests on this address. The benefit is that, should the active node fail, another router can seamlessly take over. This provides the benefits listed in (b), (c) & (d) above. Hosts only have a single default gateway, pointing to the virtual router IP, so (a) is incorrect.
- A system in your enterprise does not support individual user passwords but multiple administrators require access to the system at least once each month. Which of the following is the BEST solution to provide user accountability?
(a) Isolate the legacy system to its own VLAN
(b) Change the password weekly and manually share it with authorised users
(c) Utilise an enterprise password manager with password sharing features
(d) Remove the system from the network until a replacement can be identified
(e) Assign one admin to perform all tasks on the system
Answer:
(c)
Explanation:
An enterprise password manager with password sharing features, such as CyberArk, can effectively allow you to “check out” a password; CyberArk will give you the password to log into the system, and when you are done, CyberArk will automatically change the password. This provides accountability while using a shared account.
Tough Questions 71-120
- Which of the following key lengths are available in the Rijndael encryption algorithm (Select all that apply)
(a) 64 bits
(b) 72 bits
(c) 128 bits
(d) 112 bits
(e) 168 bits
(f) 192 bits
(g) 256 bits
(h) 512 bits
Answers:
(c), (f), (g)
Explanation:
Technically, Rijndael supports key lengths of 128 bits up to 256 bits, in 32-bit increments, but the AES standard (which uses Rijndael) stipulates only 128, 192 or 256 bit keys.
- Which of the following are symmetric algorithms?
(a) Serpent
(b) RSA
(c) MQV
(d) Blowfish
(e) RC5
(f) Diffie-Hellman
Answers:
(a), (d), (e)
- Two different companies are preparing to connect their offices together via an Internet VPN. Before establishing the connection and beginning to share data, which of the following should be in place?
(a) ISA
(b) SLA
(c) BIA
(d) DLP
(e) IDS
Answer:
(a)
Explanation:
An ISA (Interconnection Security Agreement) is used when connecting two organisations with different policies etc. This covers what is going to be accessed, the extent of which, and how it’s going to be secured.
- Which of the following is a characteristic of ‘star’ topologies
(a) Collision-free
(b) Resistant to multi-node failure
(c) Can only be used with copper cabling
(d) Limited reliance on a central aggregating device
Answer:
(b)
Explanation:
(a) would be true only if the network was implemented using a switch, rather than a hub (both are allowed by the star topology, although hubs are very rarely used in modern networks)
(b) is true because each node has its own connection to the switch/hub, so the failure of one node (or multiple nodes) wouldn’t affect the remaining nodes
(c) the topology does not specify a media type
(d) the star topology relies completely on the central switch/hub
- Which of the following is NOT one of the five rules of evidence?
(a) Admissible
(b) Authentic
(c) Complete
(d) Auditable
(e) Reliable
(f) Believable
Answer:
(d)
- Which of the following is an example of tunnelling network traffic?
(a) NAT-T
(b) Masquerading
(c) PAT (Port Address Translation)
(d) SOCKS Proxy
(e) Stateless NAT64
Answer:
(a)
Explanation:
NAT-T = NAT Traversal is a technique that, in essence, allows you to “smuggle things” (tunnel) through an address translator. If you have a type of traffic that is not translatable (of which there are many), one of the things you can do is encapsulate it within something that is translatable.
With a SOCKS proxy, you establish a connection to the proxy, which in turn goes and fetches the data. There is no tunnelling involved.
NAT64 (available in stateful and stateless flavours) is an IPv6-IPv4 translation technique, not a tunnelling technique.
- You are evaluating the merits of differential & incremental backup strategies. Which of the following is true?
(a) Differentials begin with a full backup, incrementals do not
(b) Incremental backups do not evaluate the archive bit when determining if a file should be backed up
(c) Differential backups only backup files modified since the previous differential or full backup
(d) Compared to differentials, a complete restore will take longer if using an incremental strategy
(e) A ‘copy’ backup cannot be used if using a differential backup strategy
Answer:
(d)
Explanation:
(b) is incorrect – both differential & incremental evaluate the archive bit, although only full & incremental reset the archive bit
(c) is incorrect because differential backups backup files since the previous full backup (or the previous incremental backup), not the previous differential backup
(e) Note that a copy backup is just a full backup that doesn’t reset the archive bit
- 802.2 and 802.3 correspond to which of the following standards? (Choose two)
(a) 802.2 is a security standard for port-based access control
(b) 802.3 is an Ethernet standard for Media Access Control (MAC)
(c) 802.2 is a LAN standard for token ring
(d) 802.3 is a standard for wireless LANs
(e) 802.2 is an Ethernet standard for Logical Link Control (LLC)
(f) 802.3 is a standard for Bluetooth
(g) 802.2 is a standard for WiMAX
Answers:
(b), (e)
- Which of the choices listed in NOT a characteristic of IPv6?
(a) Fixed-size header
(b) No IPv6 header checksum
(c) 128-bit source address
(d) 16-bit TTL field in header
(e) Extension Headers
(f) 20-bit Flow Label
Answer:
(d)
Explanation:
(a) IPv6 has a fixed-size header of 40 bits, unlike IPv4 with a variable size header
(b) IPv6 does not have a header checksum, unlike IPv4
(c) IPv6 addresses are 128 bits long
(d) IPv6 has no TTL (Time-To-Live) field – it is now called Hop Limit, and it’s a 8-bit field (as was the TTL field in IPv4)
(e) IPv6 has an Extension Headers field which essentially replaces the IPv4 Protocol ID field
- IPSec is comprised of a number of different protocols which work collectively to establish a level of security desired by a system administrator. Which of the following components of an IPSec connection is responsible for authenticating parties & establishing security associations?
(a) Authentication Headers (AH)
(b) Encapsulating Security Payload (ESP)
(c) Internet Key Exchange (IKE)
(d) User Datagram Protocol (UDP)
(e) Diffie-Hellman Key Exchange (DH)
Answer:
(c)
- Which of the following algorithms were considered by NIST to become the new Advanced Encryption Standard? (Choose four)
(a) RC6
(b) Blowfish
(c) Twofish
(d) Serpent
(e) scrypt
(f) Rijndael
(g) Whirlpool
(h) SHA-512
Answers:
(a), (c), (d), (f)
Explanation:
MARS was the other AES finalist, and of course Rijndael was the eventual winner.
- Which of the following best describes the domain of a relation in a relational database?
(a) A named set of possible values for an attribute, all of the same type
(b) All tuples in a relation
(c) All the attributes of a relation
(d) The cardinality of a relation
(e) The degree of attributes in a relation
Answer:
(a)
Explanation:
Relation = table
Attribute = column
Tuple = row
Cardinality = number of rows (tuples)
Degree = number of columns (attributes)
The domain of a relation (table) is all possible values of a column (attribute)
- Both IPv4 and IPv6 operate at Layer 3 of the OSI model. Which of the following is NOT a field in an IPv4 header?
(a) TTL
(b) Protocol ID
(c) Flow Label
(d) Version
(e) Source IP Address
(f) Fragment Offset
(g) Checksum
Answer:
(c)
Explanation:
Flow Label is a field in an IPv6 header, but does not exist in an IPv4 header
TTL, Protocol ID, Fragment Offset & Checksum are in IPv4, not IPv6
Version & Source IP address are in both
- Which of the following firewall types provides you the LEAST amount of control over network traffic?
(a) Application layer firewalls
(b) MAC filters on an L2 switch
(c) Packet filtering routers
(d) Stateful firewalls
(e) Proxy servers
Answer:
(c)
Explanation:
(a) gives a large amount of control
(b) is not a firewalling technique
(c) examine the source and/or destination of traffic at Layer 3 and/or 4, but that’s it (they don’t look at the payload, the relationship of one packet to another packet, whether it’s part of an established connection – every packet is evaluated in isolation)
(d) typically operate on the same sort of logic as (c) but take it a step further by maintaining a state table to determine traffic passing through the device and dynamically create reciprocal entries – greater level of control with lower administrative effort
(e) offer a higher level of control than (c)
- By what mechanism does an IPv6 node resolve an IP address to a MAC address?
(a) Using the Address Resolution Protocol
(b) Using mDNS for local name resolution
(c) Using Solicited Node Multicast Address
(d) Using SLAAC
(e) Sending a multicast query to FF02::1
(f) IPv6 does not use MAC addresses
Answer:
(c)
Explanation:
(a) ARP does not exist in IPv6.
(b) mDNS is multicast DNS (often used as a replacement for NetBIOS)
(c) IPv6 resolution of IP address to MAC address is via an ICMP multicast to a Solicited Node Multicast Address, a fixed 104-bit value concatenated with the low order 24 bits of the IP address you’re looking for. In most circumstances (although not guaranteed), this will produce a unique multicast address, meaning there is a high degree of likelihood that only the node you’re looking for will receive the solicitation (unlike ARP which broadcasts indiscriminately) – more efficient and marginally more secure.
(d) SLAAC (StateLess Address AutoConfiguration) is the mechanism by which IPv6 nodes can automatically configure themselves, given an address prefix.
(e) FF02::1 is the all-nodes multicast address on an IPv6 local segment (the closest to an IPv4 broadcast, as broadcasts don’t exist in IPv6) but isn’t the method used to resolve an IP address to MAC address
(f) MAC is an Ethernet concept residing at Layer 1, so IPv6 still has to use MAC addresses
- An IT contigency planning process consists of seven broad steps. Which of the following is one of those steps? (Choose two)
(a) Define metrics to be gathered
(b) Develop recovery strategies
(c) Respond to management with mitigation steps
(d) Perform functional & security testing
(e) Identifying preventive controls
(f) Obtain formal authorisation to operate (ATO)
Answers:
(b), (e)
- Which of the following RAID solutions provides the SMALLEST net usable space?
(a) RAID 0
(b) RAID 1
(c) RAID 3
(d) RAID 5
Answer:
(b)
Explanation:
(a) provides the most space, no redundancy
(b) you lose half of your disk space
(c) you lose 1/x disk space (i.e. if you have 3 disks, 1/3rd)
(d) you lose 1/x disk space (minimum of 3 disks, so 1/3rd)
- What is the purpose of a Hamming code?
(a) It is used for data transposition in encryption processes
(b) It is used as a data encoding mechanism for 802.11 WLANs
(c) It is used to detect & correct errors in data
(d) It is used to calculate CRC checksums in Ethernet frames
Answer:
(c)
Explanation:
Often used in RAID to provide parity.
- Your organisation has been allocated a public network with a /28 prefix. There are 2,000 employees. You need to provide Internet connectivity for workstations, mobile devices and on-site Windows & Linux servers. Which of the following will allow this?
(a) NAT: configure static translations
(b) PAT: translate MAC, IP & TCP/UDP ports
(c) HTTP proxy: forward all Internet traffic to the proxy
(d) NAT: translate IP addresses dynamically from a pool
(e) PAT: translate IP & TCP/UDP ports to one or more public addresses
(f) SOCKS proxy: relay all device traffic through the proxy
Answer:
(e)
Explanation:
(a) The /28 prefix only gives you 14 public addresses, and you would need 2,000+ to configure static translations.
(b) PAT does not translate MAC addresses
(c) would only support HTTP, not all Internet services
(d) still wouldn’t work because you only have a pool of 14 public addresses between 2,000 devices
(e) PAT (which most people colloquially call NAT) will allow you to share one or more public addresses among multiple nodes
(f) is a viable solution but not the norm these days, and it’s not easy to configure devices
- Which of the following is a key concern for ephemeral Diffie-Hellman key exchanges?
(a) Forward secrecy is not available
(b) No authentication
(c) Weak encryption
(d) ‘Long-term’ private key compromise allows for viewing of data
Answer:
(b)
Explanation:
(a) Ephemeral Diffie-Hellman provides forward secrecy by generating new per-session keys each time you do a key exchange
(b) Both ephemeral and standard Diffie-Hellman don’t natively support authentication
(d) The private key is ephemeral so this is not true (even in static DH, a compromise of the long-term key would not allow for viewing of the data)
- Which audit framework and methodology focuses on the delivery of capability rather than focusing on a specific technology?
(a) COBIT
(b) ISO 27000
(c) ITIL
(d) COSO
Answer:
(b)
- Select the FOUR correct steps from the following list, and put them in order of a federated identity connection using SAML.
(a) Get SAML token
(b) Authenticate
(c) Generate SAML key
(d) Request access to resources
(e) Validate token
Answers:
(b), (a), (d), (e)
Explanation:
User authenticates, gets a SAML token and requests access to resources. The service will then validate the token, and then the access is provided.
Generating a SAML key is not part of this process.
- Which of these in-transit encryption types can be either symmetric or asymmetric?
(a) Circuit encryption
(b) Link encryption
(c) Tunnel encryption
(d) Transport encryption
Answer:
(d)
Explanation:
Link & tunnel encryption are based on symmetric encryption.
Transport encryption can be based on either symmetric or asymmetric encryption.
Circuit encryption is a distractor answer.
- The method of controlling which traffic is forwarded between network segments is commonly known as:
(a) Network perimeters
(b) Network segregation
(c) Network partitioning
(d) Network boundaries
Answer:
(c)
- An ACK storm starts with a(n) ______, confusing the receiving system since there is no preceding SYN or FIN flagged packet.
(a) SYN/ACK
(b) SYN
(c) FIN
(d) ACK
Answer:
(d)
- Which type of proxy can be defined as being able to relay traffic from a trusted end-point running a specific application to an untrusted end-point?
(a) Reverse proxy
(b) Application-level proxy
(c) Transparent proxy
(d) Suffix proxy
Answer:
(b)
Explanation:
The two basic types of proxies are:
– circuit-level, which creates a conduit through which a trusted host can communicate with an untrusted host, and encompasses a number of protocols
– application-level, which relays traffic from a trusted endpoint, running through a specific application to an untrusted end-point
- Which of the following is NOT considered a class of instant messaging presented to the public?
(a) Server-oriented networks
(b) Brokered communication
(c) Peer-to-peer networks
(d) Point-to-point tunnelling
Answer:
(d)
Explanation:
Instant messaging systems can generally be categorised in three classes: peer-to-peer networks, brokered communication, and server-oriented networks.
- Of the following, which is an example of multi-factor authentication? (Select all that apply)
(a) A split-knowledge system
(b) A username with an iris scan
(c) A smartcard and a PIN
(d) A password and a PIN
(e) A passphrase and a CAPTCHA challenge
(f) A passphrase and a Pre-Shared Key
Answer:
(c)
Explanation:
There is in fact only one correct answer.
(a) A split-knowledge system involves a password being split into two or more parts, where only one person knows each part. It’s still single factor.
(b) This is considered single-factor – an iris scan is “something you are” but a username doesn’t qualify as “something you know” since it’s considered public information
(c) A smartcard is “something you have” and a PIN is “something you know”, so this qualifies
(d) A password and a PIN are both “something you know” – two of the same factor is considered single factor
(e) CAPTCHA is not an authentication factor
(f) As (d), both “something you know”
- As it relates to the EU’s General Data Protection Regulation, which of these have been added (to what was already included in the EU Data Protection Directives) under the requirement to protect Personally Identifiable Information?
(a) Physical/physiological characteristics
(b) Genetics
(c) Identification number
(d) Mental status
(e) Location data
(f) Economic status
(g) Cultural or social identity
(h) Online identifiers
Answers:
(e), (h)
Explanation:
(a), (b), (c), (d), (f) & (g) already existed in the DPD
(e) & (h) were not in the DPD but are now part of GDPR
- Which of the following is a NEW requirement for the EU General Data Protection Regulation (GDPR)?
(a) Data cannot be disclosed without data subject’s consent
(b) Data can only be used for the purpose stated when collected
(c) Subjects can access their data and make corrections when inaccurate
(d) Subjects have the right to be forgotten
(e) Subjects must consent to data collection
(f) Collected data should be kept secure from potential abuse
Answer:
(d)
Explanation:
All the other options are included in GDPR, but also existed prior to GDPR.
- Which of the following is a violation of the principle of least privilege? (Select all that apply)
(a) Giving an auditor read & write permissions for system log files
(b) Installing access control units on elevators, limiting staff to job-related floors
(c) Requiring users to enter only a username and password to log into a system
(d) Placing a Linux sysadmin in the Domain Admins group in Active Directory
(e) Granting software developers access to production systems
Answers:
(a), (d)
Explanation:
(e) is not a violation of least privileges – remember, software developers are people too, so likely require access to production systems e.g. email, but this is in their capacity as regular users. Granting software developers access to production systems in their role of software developers is a problem, but would be a violation of separation of duties, not of least privilege.
- Confidentiality is a critical component of modern distributed computing systems. Which of the following represents the greatest challenge to providing confidentiality for such an environment?
(a) Heterogeneity of systems
(b) Lack of protocol standardisation
(c) Network scalability
(d) Inadequate system transparency
(e) Missing digital signatures
(f) Transmitting unencrypted data
Answer:
(f)
Explanation:
(a) & (b) are valid concerns, but are more related to interoperability/availability than confidentiality
(f) In a distributed computing system, you may have a secure connection to the node you’re immediately accessing, but this may send/receive unencrypted data further along the chain – do you have a guarantee of end-to-end encryption?
- Which of the following is NOT an element of the risk analysis process?
(a) Analysing an environment for risks
(b) Creating a cost/benefit report for safeguards, to present to upper management
(c) Selecting & implementing appropriate safeguards
(d) Evaluating each threat’s likelihood of occurring, and cost of damage
Answer:
(c)
Explanation:
Selecting safeguards is a task of upper management, based on the results of risk analysis. It falls under the wider risk management piece, but is not part of the risk analysis process.
- Which of the following represents accidental or intentional exploitations of vulnerabilities?
(a) Threat events
(b) Risks
(c) Threat agents
(d) Breaches
Answer:
(a)
- When a safeguard or a countermeasure is not present, or not sufficient, what remains?
(a) Vulnerability
(b) Exposure
(c) Risk
(d) Penetration
Answer:
(a)
Explanation:
Remember that vulnerability is the absence or weakness of a countermeasure.
- The Active Directory domain administrator has created a security group called “Project Z”, and added members of the Project Z team to the group. He then configures a Group Policy Object that allows only that group to access Project Z servers on the network. What type of access control is this an example of?
(a) Discretionary access control
(b) Context-dependent access control
(c) Non-discretionary access control
(d) View-based access control
Answer:
(c)
Explanation:
This is an example of role-based access control – granting privileges to roles, and adding users to those roles. RBAC is a type of non-discretionary access control.
Discretionary access control is granting users direct privileges, and context-dependent access control uses various metrics to control access (e.g. time of day).
View-based access control is associated with databases: creating constrained views to limit what users can see.
- You are developing an attack tree for a web application, and as part of the process you are attempting to anticipate your potential attackers. Which of the following will you need to identify in order to accurately characterise a likely adversary? (Choose three)
(a) Ease of vulnerability discovery
(b) Attacker motive
(c) Damage potential
(d) Opportunity
(e) Trust boundaries
(f) Means
(g) Exploitability
Answers:
(b), (d), (e)
Explanation:
Motive, opportunity & means (MOM!) are the three elements to characterise attackers.
(a), (c) & (g) are elements of the DREAD model for assessing risk, not attackers.
Trust boundaries are an element of the STRIDE threat modelling methodology.
- Which of the following are generally not included in BIA recovery timeframe assessments? (Select two)
(a) RPO
(b) MTBF
(c) MTD
(d) RTO
(e) MTBSI
(f) TTR
Answers:
(b), (e), (f)
Explanation:
MTBF (Mean Time Between Failures) and MTBSI (Mean Time Between Service Incidents) are not included in BIA recovery timeframe assessments.
TTR is is distractor answer.
- What are the four main steps of the business continuity planning process, in the correct order?
(a) Business organisation analysis, project scope & planning, continuity planning, approval & implementation
(b) Project scope & planning, business organisation analysis, continuity planning, approval & implementation
(c) Project scope & planning, business impact assessment, continuity planning, approval & implementation
(d) Business impact assessment, project scope & planning, continuity planning, approval & implementation
Answer:
(c)
- What critical components should be included in your business continuity training plan? (Select all that apply)
(a) Specific training for individuals with direct involvement (e.g. members of BCP team)
(b) Specific training for individuals with indirect involvement
(c) Specific training for all employees
(d) Plan overview briefing for all employees
Answers:
(a), (b), (d)
Explanation:
The BCP training plan should include a plan overview briefing for all employees, and specific training for individuals with direct or indirect involvement with BCP activities. Specific training (beyond an overview briefing) is not generally required for all employees.
- What is the first step that individuals responsible for the development of a business continuity plan should perform?
(a) BCP team selection
(b) Business organisation analysis
(c) Resource requirements analysis
(d) Legal & regulatory assessment
Answer:
(a)
- Once the BCP team is selected, what should be the first item placed on their agenda?
(a) Business impact assessment
(b) Business organisation analysis
(c) Resource requirements analysis
(d) Legal & regulatory assessment
Answer:
(b)
- What will be the major resource consumed during the BC planning phase?
(a) Hardware
(b) Software
(c) Processing time
(d) Personnel
Answer:
(d)
- Which task of BCP bridges the gap between the BIA and the continuity planning phases?
(a) Resource prioritisation
(b) Likelihood assessment
(c) Strategy development
(d) Provisions & processes
Answer:
(c)
- In which BCP task would you actually design procedures & mechanisms to mitigate risks deemed unacceptable by the BCP team.
(a) Strategy development
(b) Business impact assessment
(c) Provisions & processes
(d) Resource prioritisation
Answer:
(c)
- What type of mitigation provision is utilised when redundant comms links are installed?
(a) Hardening systems
(b) Defining systems
(c) Reducing systems
(d) Alternative systems
Answer:
(d)
Explanation:
The two main mitigation provisions for systems (and indeed facilities) are hardening systems and alternative systems. Hardening systems refers to improving protection of existing systems, while alternative systems include redundant components, systems, links or entire facilities.
- Which of the following are characteristics of both TCP and UDP? (Choose two)
(a) Both use sequence and acknowledgement
(b) Both can carry DNS payloads
(c) Both implement windowing
(d) Both implement a header checksum
(e) Both use control bits to track connection state
Answers:
(b), (d)
Explanation:
TCP is a connection-oriented protocol with all of the above characteristics.
UDP is a connectionless protocol so does not implement (a), (c) & (e). It does implement a header checksum.
Note that header checksums only check integrity of the header, not the payload. IPv4 also uses a header checksum, IPv6 does not – but TCP/UDP over IPv6 still retains its header checksum.
DNS uses UDP port 53 for lookups and TCP port 53 for zone transfers (it can also be configured to use TCP for lookups, but this is not the default).
- An organisation that uses PIV cards for desktop computer logins and physical access to locations in the facility wants to extend PIV-based authentication to the increasing number of company-issued smartphones & tablets. Which of the following will provide the BEST authentication security and the MOST seamless user experience?
(a) MicroSD authentication tokens
(b) TOTP authentication using a key fob or mobile app
(c) Derived PIV credentials stored security on device
(d) USB PIV card reader connected to device
Answer:
(c)
Explanation:
A PIV card (or CAC – Common Access Card) is a FIPS 401 compliant smart card. Derived PIV allows you to run a virtual PIV card on your mobile or desktop device, and would be the most secure and certainly most seamless option here. (a) is not really a practical answer, (b) is not seamless and (d) would work but using an external card reader with a mobile device would be cumbersome.
- You have been tasked with reducing the likelihood that nodes in your network can forward packets with spoofed source IP addresses. Which of the following is the BEST way to accomplish this?
(a) Use SNMP to generate a list of allowed MACs for each VLAN
(b) Implement ACLs on each router interface, allowing only traffic sourced from the local segment
(c) Enable MLD snooping on Layer 2 switches
(d) Configure Reverse Path Forwarding on the routers
Answer:
(d)
Explanation:
(a) would not help and neither would (c) – MLD snooping is a multicast distribution technique that is outside of the scope of CISSP.
(b) would work but is very labour-intensive and error prone
(d) Reverse Path Forwarding is essential where a router examines the source address of the packet presenting at the network interface, and asks “if I were sending a packet TO this address, would I send it from this interface”? If the answer is no, the packet is highly likely to be spoofed, and will be dropped.
- Which criminal law was the first to implement penalties for the creation of viruses, worms & other types of malicious code that cause harm to computer systems?
(a) Computer Security Act
(b) National Infrastructure Protection Act
(c) Computer Fraud & Abuse Act
(d) Electronic Communications Privacy Act
Answer:
(c)
Things To Remember
Domain 1: Security & Risk Mgmt
Governments tend to prioritise confidentiality, private companies often favour availability.
DAD is the inverse of CIA:
– Disclosure is the inverse of Confidentiality
– Alteration is the inverse of Integrity
– Destruction is the inverse of Availability
Operational Technology systems (PLCs, SCADA) tend to prefer availability, then integrity, then finally confidentiality – AIC triad.
Accountability (and security in generally) must be legally defensible
Protection mechanisms include layering, abstraction, data hiding.
Strategic plan: ~5 yrs (update annually)
Tactical plan: 6-12 mths
Operational plan: short term, highly focused (update mthly/qtly)
Policies can be organisational, issue-specific or system specific.
Policies can be regulatory (req’d by industry or legal standards), advisory (define acceptable behaviours/activites & consequences of violations) or informative.
Most policies are advisory.
Advisory/informative does not mean optional – all policies are compulsory.
Due care & due diligence
Due care – doing the right thing; Prudent Man rule; senior mgmt ultimately responsibility
Due diligence – practicing activities to maintain due care
Classification scheme implementation steps
- Identify custodian; define their responsibilities
- Specify evaluation criteria (how information will be classified & labelled)
- Classify & label each resource (owner conduct, supervisor reviews)
- Document any exceptions discovered to the classification policy; update evaluation critera
- Select controls to be applied to each classification level
- Specify procedures for declassifying resource, as well as for transferring to an external party
- Enterprise-wide awareness of classification system
Note that marking of hardware assets (computers, backups) with classification labels is commonplace and good security practice.
Some DLP tools can automatically apply protection based on labels applied by users (e.g. to email messages).
Military classification scheme
U.S. Can Stop Terrorism
Unclassified
Sensitive (SBU)
Confidential [would cause damage]
Secret [would cause serious damage]
Top Secret [would cause exceptionally grave damage]
Classified = Confidential (lowest), Secret, Top Secret (highest)
A classification authority is the entity that applies the original classifcation to sensitive data. In the US, only the president, vice president, and agency heads can classify data (although they can delegate this permission to others).
Private sector classification scheme
Public
Sensitive
Private (personal info of employees)
Confidential
“Sensitive” label can mean different things in different organisations (no prescribed single classification scheme for private sector), but for the exam: sensitive refers to any information that isn’t public or unclassified.
Data classifications are typically defines within security policies or data policies.
Sensitivity vs criticality
- Sensitivity describes the amount of damage that would be done should the information be disclosed – i.e. concerned with confidentiality.
- Criticality describes the time sensitivity of the data – i.e. concerned with availability.
Security roles
Senior Manager (organisational owner) – responsible for due care & due diligence
Security Professional (infosec officer) – delegated tasks such as writing & implementing policy (not decision making)
Data Owner – responsible for classifying info (typically a manager)
Data Custodian – delegated task of implementing protection defined by policy
User – follows policy
Auditor – reviews & verifies policy
Threat modelling
Proactive (defensive) approach: predict threats and build defences into design – more cost effective, but not all threats can be foreseen
Reactive (adversarial) approach: respond to threats/vulnerabilities as discovered (e.g. by pen testing, source code review or fuzz testing)
SD3+C
“Secure by Design, Secure by Default, Secure in Deployment + Communication” (Microsoft)
Aims to reduce vulnerabilities and reduce impact of any that remain.
Identifying threats
Focused on assets, focused on attackers or focused on software.
STRIDE
Microsoft again!
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial of service
- Elevation of privileges
PASTA
- DO: Define Objectives
- DTS: Define Technical Scope
- ADA: Application Decomposition & Analysis
- TA: Threat Analysis
- WVA: Weakness & Vulnerability Analysis
- AMS: Attack Modelling & Simulation
- RAM: Risk Analysis & Management
Objectives -> scope -> app analysis -> threats -> weaknesses -> attacks -> risks
Other threat modelling concepts
Trike: Risk-based approach.
VAST: Visual, Agile & Simple Threat.
Reduction analysis/decomposition
Key concepts:
- Trust boundaries
- Data flow paths
- Input points
- Privileged operations
- Details about security stance & approach
Prioritisation & response
Probability * Damage Potential: Score both from 1-10, multiply for total score of 1-100
High, Medium, Low
DREAD:
- Damage potential
- Reproducibility
- Exploitability
- Affected users
- Discoverability
SSAE/SOC audits
- SSAE 18 replaced SSAE 16 in 2017
- SOC-1 audit: internal controls over financial reporting
- SOC-2 audit: assesses CIA of security controls (shared under NDA)
- SOC-3: same as SOC-2, but publicly available
(ISC)2 canons
To be applied in order (remember longest to shortest):
- Protect society, the commonwealth & the infrastructure
- Act honourably, honestly, justly, responsibly & legally
- Privide diligent & competent service to principals
- Advance & protect the profession
Privacy definitions
- Active prevention of unauthorised access to PII
- Freedom from unauthorised access to information deemed personal or confidential
- Freedom from being observed, monitored or examined without consent or knowledge
Quantitative RA
SLE = AV * EF
ALE = SLE * ARO
Cost Benefit Analysis:
Value = ALE before safeguard – ALE after safeguard – annual cost of safeguard
Residual risk = cost of applying extra countermeasures is more than the estimated loss resulting from a threat/vulnerability
Controls gap = amount of risk reduced by implementing controls
TOTAL RISK – CONTROLS GAP = RESIDUAL RISK
Controls
Compensating: substitute for loss of primary controls
Corrective: mitigate damage (e.g. backups)
Recovery: restore to normal after incident
Functional order: Deter -> Deny -> Detect -> Delay
BCM/BCP
Business continuity planning processes [EXAM]
- Project scope & planning
- Acquire BCP policy stmt from senior mgmt
- Business Organisational Analysis (BOA) [EXAM]
- helps identify potential BCP team members and provides the foundation for the remaining processes
- evaluates depts responsible for core services, as well as critical support services such as IT, physical security facilities & maintenance
- identifies senior execs and other key individuals essential for the ongoing viability of the organisation
- BCP team creation – include: [EXAM]
- a project mgr
- representation from senior mgmt, IT, InfoSec, HR, PR, legal & core services depts identified in BOA
- a representative from each of the functional areas identified by the BOA
- Assessment of resources (and commitment from snr mgmt to support the BCP process)
- Analysis of legal & regulatory landscape [EXAM]
- including due diligence to protect shareholder interests, contractual requirements with clients, and any industry-specific laws/regulations that mandate specific BCP procedures
- Business impact assessment
- Continuity planning
- Approval & implementation
Business Impact Assessment (BIA)
- Identifies critical resources, and the threats posed to them
- Assesses likelihood of each threat occurring, and the impact this would have
- Provides measures to help prioritise the commitment of resources
- Quantitative vs qualitative
- Remember to include any cloud vendors on which the organisation relies
- Contract is not sufficient due diligence
- Need to verify sufficient controls are in place – often not possible to perform a site visit, so many cloud providers can provide a SOC-2 or SOC-3 report (SOC-1 reports don’t work as they are for internal financial controls only!)
- Steps of BIA: [EXAM]
- Identify business priorities (criticality prioritisation)
- Start with a qualitative list, ordered by priority
- Assign quantitative AV (asset value) to each asset
- Calculate MTD for each business function, and decide upon an achievable RTO (that is less than the MTD)
- Risk identification
- Natural, e.g. earthquakes, hurricanes, tornadoes, storms
- Man-made e.g. terrorism, theft/vandalism, arson, service provider outages
- This stage is purely qualitative
- Likelihood assessment
- Assign ARO to each risk
- Expert advice is sometimes available for free, e.g. USGS earthquake hazard map
- Your insurance company may be able to share some of the risk likelihood information they have compiled
- Impact assessment
- Assign EF to each asset (e.g. percentage of the facility that will be lost if there is a fire)
- Calculate the SLE (AV * EF) and ALE (SLE * ARO) for each risk
- Difficult to put dollar values on qualitative aspects such as loss of goodwill among client base, employee attrition & negative publicity, but important to do so at this quantitative stage so they don’t get lost or forgotten, and can be included in the next (and final) stage
- Resource prioritisation
- Sort the list of risks analysed during the BIA process in descending order by ALE
- Select as many items as you’re willing and able to address simultaneously, and work your way down until you run out of risks (unlikely!) or resources (much more likely!)
- Merge the list with the results of any qualitative concerns identified in the BIA (an art, not a science – relies on expertise of BCP team & input of senior mgmt)
- Qualitative concerns may justify elevating or lowering the priority of risks that are already on the ALE-sorted quantitative list.
- Identify business priorities (criticality prioritisation)
Continuity planning steps [EXAM]
- Strategy development
- Bridges gap between BIA and continuity planning phases
- Take the output of BIA resource prioritisation process and decide which risks will be address by the BCP
- Look at MTD estimates created earlier, and determine which risks are deemed acceptable
- Determine which risks require mitigation, and the level of resources that will be committed to each mitigation task
- Provisions & processes
- The meat of the entire BCP
- BCP team designs the specific procedures and mechanisms to mitigate risks that were deemed unacceptable during the previous phase
- Covers three categories of assets:
- People
- Human safety is always the first priority, including before, during and after an emergency
- Next you must make provisions to allow your employees to conduct their BCP & operational tasks in as normal a manner as possible
- Think about arrangements for shelter and food, if your BCP requires people to be present in the workplace for extended periods – maintain stockpiles & rotate to prevent spoilage
- Buildings & facilities
- Many businesses require specialised facilities such as offices, manufacturing plants, warehouses etc
- BCP should outline hardening provisions: mechanisms & procedures that can be put in place to protect your facilities against the risks identified in the strategy development phase. Examples range from patching a leaky roof to installing hurricane shutters & fireproof walls.
- In the event that it’s not feasible to harden a facility against a risk, your BCP should identify alternate sites where business activities can resume (immediately, ore at least within a period shorter than the MTD for all critical functions)
- Infrastructure
- Every business depends on some sort of infrastructure for its critical processes – often IT in the form of systems that process orders, manage the supply chain and perform other business functions, as well as the communications backbone
- The BCP must address how these systems will be protected against risks identify during the strategy development phase
- As with buildings, there are two main methods of providing this protection:
- Physically hardening systems by introducing protective measures such as fire suppression and UPS
- Introducing alternative systems to provide redundancy (either redundant components or completely redundant systems/comms links)
- Applies to whatever infrastructure components serve your critical processes – transportation, utilities, banking systems etc. – not just IT
- People
- Plan approval
- Plan should be approved by highest level executive possible – ideally the CEO
- Demonstrates importance of the plan to the entire organisation, as well as give it greater credibility to other senior managers
- Plan implementation
- Training & education
- should include a plan overview for all staff, and specific training for individuals with direct or indirect involvement in the BCP
BCP documentation
Committing your BCP methodology to paper is critical, and provides several important benefits:
- Ensures that BCP personnel have a written document to reference in the event of an emergency, regardless of the availability of senior BCP members
- Provides a historical record of the BCP process that will be useful to future personnel seeking to understand the reasoning behind various procedures, and implement necessary changes in the plan
- Forces the team members to think clearly about their thoughts, which often reveals flaws in the plan – it also allows draft documents to be distributed outside of the BCP team for a “sanity check”
Some important elements of a written BC plan include:
- Continuity planning goals
- To be decided at (or before) the first BCP team meeting
- Likely to remain unchanged throughout the life of the BCP
- Most common goal is simply to ensure the continuous operation of the business in the face of an emergency situation
- Other goals may be included to meet organisational needs
- Statement of importance
- Commonly takes the form of a letter to the organisation’s employees stating the reason that the organisation devoted significant resources to the BCP development process, and requesting the cooperation of all personnel in the BCP implementation phase
- This is where senior exec buy-in comes into play: ideally this letter should be signed by the CEO
- Statement of priorities
- Flows directly from the “identify priorities” element of the BIA
- Simply involves listing critical functions, ordered by priority
- Statement of organisational responsibility
- Also comes from a senior-level exec and can be incorporated in the same letter as the statement of importance
- Basically echoes the statement that “BC is everyone’s responsibility!”
- Statement of urgency & timing
- Expresses the criticality of implementing the BCP
- Outlines the implementation timetable decided upon by the BCP team and agreed by upper mgmt
- Can be included in the same letter as the statement of importance & statement of organisational responsibility, in which case the timetable should be included as a separate document
- Risk assessment
- Summaries the decision-making process undertaken during the BIA
- Should include a discussion of all the risks considered, as well as the quantitative & qualitative analyses performed against them
- including actual AV, EF, ARO, SLE & ARO figures, for the quantitative analysis
- the thought process behind the quantitative analysis should also be provided
- This section must be updated on a regular basis because it reflects a point-in-time assessment
- Vital records program
- Document outlining where critical business records will be stored, and the procedures for making & storing backups
- One of the biggest challenges in implementing a VRP is identifying the vital records in the first place!
- Ask functional leaders what they would need if they were to rebuild the organisation from scratch, forcing them to visualise the actual process and walk through the steps in their mind
- Emergency response guidelines
- Outline the organisation & individual responsibilities for immediate response to an emergency situation, including:
- Immediate response procedures (security & safety procedures, fire suppression procedures, notification of emergency response agencies etc)
- List of individuals to be notified of the incident (execs, BCP team members etc)
- Secondary response procedures that first responders should take while waiting for BCP team to assemble
- Should be easily accessible to everyone in the organisation who may be first responders in a crisis incident – when disaster strikes, time is of the essence, and any delay in activating your BC procedures may lead to undesirable downtime for your business operations
- Outline the organisation & individual responsibilities for immediate response to an emergency situation, including:
- Maintenance
- BCP documentation and the plan itself must be living documents
- BCP team should not be disbanded after plan is developed; they should meet periodically to discuss, review & update the plan
- Minor changes can be made by unanimous consent, but drastic changes to an organisation may require starting the full BCP development process from scratch
- Practice good version control and ensure all older versions of the BCP in existence are physically destroyed & replaced
- Testing & exercises
- A formalised exercise program should be outlined in the BCP documentation.
Note on overall BCP resource requirements
- BCP Development: The major resource consumed by this phase will be effort expended by members of the BCP team and supporting staff.
- BCP Testing, Training & Maintenance: Will require some hardware & software commitments, but again the major commitment in this phase will be effort on the part of the the employees involved in these activities.
- BCP Implementation: A full implementation of the BCP (i.e. when disaster strikes) will require significant resources, including a large amount of effort and the utilisation of hard resources (primarily funding but possibly also hardware/software, other goods and even buildings)
Types of BC/DR test
- Checklist: Copies of plans distributed to different departments; functional managers review.
- Structured walkthrough: Representatives of each dept go over the plan; think “read–through”; also known as table-top test
- Simulation test: Going through an imaginary disaster scenario, stop short of actual relocation to alternate site.
- Parallel test: Systems moved to an alternate site; a portion of processing takes place there
- Full-interruption test: Original site is shut down and all processing is moved to the alternate facility.
Laws
Criminal vs civil
- In the US, both types of law are enacted in the same way (House of Representatives & the Senate) and must comply with the Constitution
- At the federal level, both types of law are embodied in the United States Code (USC)
- Major difference is in how they are enforced – in civil matters, law enforcement authorities are normally not involved (beyond taking action necessary to restore order)
- In civil law, the plaintiff must file a lawsuit against the defendant
- Administrative law, published in the Code of Federal Regulations (CFR) is a third type of law dictating the day-to-day operations of government agencies – from procurement procedures to immigration policies
- Info sec professionals must have a basic working knowledge of laws & regulations, but if in doubt, call an attorney!
Specific laws
- Comprehensive Crime Control Act (CCCA, 1984) – first law against computer crime
- Unauthorised access of classified info
- Cause malicious damage to a federal system >$1000
- Modify medical resources
- Computer Fraud & Abuse Act (CFAA, 1986)
- Amendment to CCAA
- Increased damage threshold to $5000
- Scope increased widely from “federal systems” to “federal interest computers”
- Often criticised as over-broad – can be interpreted to criminalise violation of a website’s ToS
- 1994 additions (Computer Abuse Amendments Act): outlawed creation of malicious code, and scope of law to cover all systems used in interstate commerce
- 1996 additions (National Information Infrastructure Protection Act): now covers international as well as interstate commerce, extends protections to national infrastructure such as railways, gas pipelines, electrical grids and telecoms circuits, and treats any acts that deliberately or recklessly damage these as a felony
- Further amendments in 1996, 2001, 2002 & 2008
- Federal Information Security Management Act (FISMA, 2002):
- Requires federal agencies to implement an InfoSec program, including:
- Risk assessments
- Policies & procedures
- Awareness training
- Testing, evaluation & remediation
- Procedures for managing security incidents
- Continuity of operations plans & procedures
- IS program must include activities of contractors
- Repealed & replaced Computer Security Act (1987) and Government Information Security Reform Act (2000)
- Developed by NIST
- Requires federal agencies to implement an InfoSec program, including:
- Federal Cybersecurity Laws of 2014
- Confusingly-named Federal Information Security Modernization Act – centralised cybersec responsibility within the Department of Homeland Security [DHS] (except defence-related which remains with the Secretary of Defense, and intelligence-related with the Director of National Intelligence)
- Cybersecurity Enhancement Act – gives NIST responsibility for coordinating nationwide work on voluntary cybersecurity standards (800 series of Special Publications, and the NIST CPF: Cybersecurity Policy Framework)
- National Cybersecurity Protection Act: required the DHS to establish a national cybersecurity & comms integration centre to serve as the interface between federal agencies & civilian organisations for sharing cybersec risks, incidents, analysis & warnings
- Paperwork Reduction Act (1995)
- Requires approval before requesting info from public
- Enacted by Office of Management Budget (OMB)
- Uniform Computer Information Transaction Act (UCITA)
- Law against breach of licence agreements (e.g. EULAs)
- Federal Sentencing Guidelines (1991)
- Formalised prudent man rule (senior execs take personal responsibility)
- Organisations can minimise punishment if they can prove they exercised due diligence
- Outlines burdens of proof for negligence
Import/export
- International Traffic in Arms Regulations (ITAR)
- Controls export of items specifically designated as military & defence items
- Includes technical information relating to those items
- Items covered appear on the US Munitions List (USML)
- Export Administration Regulations (EAR)
- Cover a broader set of items that are designed for commercial use but may have military applications (including an entire category of infosec products)
- Items covered appear on the Commerce Control List (CCL) maintained by US Dept of Commerce
- Export of high-performance computing systems from the US is currently allowed to virtually any country without prior government approval (excepts include Cuba, Iran, North Korea, Sudan & Syria)
- Export of even relatively low-grade encryption was virtually impossible under previous regulations, but retail and mass-market security software may now be freely exported after a review by the Commerce Dept
Privacy-focused laws & regulations
Laws & regulations differ but typically a primary requirement is that the collection of data must be limited to only what is needed. Also, data should be obtained by lawful & fair methods, and with the knowledge and/or consent of the individual.
- HIPAA + HITECH (health)
- Not just for healthcare providers such as doctors/hospitals; any employer that provides (or supplements) healthcare policies handles PHI; in the US, employers providing/subsidising healthcare, therefore HIPAA applies to large percentage of organisations in the US
- HITECH requires a written contract agreement known as a BAA (business associate agreement) for organisations who handle PHI on behalf of a HIPAA-covered entity, and also introduces new data breach notifications (notify affected individuals, and if affecting >500 individuals, also the Secretary of Health & Human Services + the media)
- All states (apart from Alabama & North Dakota) have data breach notification laws modelled on those first introduced in California in 2002
- GLBA (financial)
- GLBA relaxed governmental barriers between financial institutions, but includes limitations on the types of information that could be exchanged (even between subsidiaries), and also requires institutions to provide written privacy policies to all their customers
- FERPA (education)
- applies to any educational institution accepting federal govt funding
- parents/students have right to inspect/correct educational records
- schools may not release personal information without written consent (with certain exceptions)
- COPPA (children’s online privacy)
- websites must have a privacy notice
- parents must be able to review any information on their children, and have the right to permanently delete it
- parents must give consent to collection of info about children <13
- CalOPPA (California Online Privacy Protection Act 2003, amended 2014)
- First US state law requiring commercial websites/online services to include a privacy policy on their website
- Applies to any service that collects personal information on California residents – in effect, potentially applies to any website in the world that collects personal information (since if it’s available on the Internet, California residents can access it)
- Most states now have a similar state law deriving from CalOPPA
- PIPEDA (Personal Information Protection & Electronic Documents Act, Canada)
- EU DPD
- Processing of data must meet one of the following criteria:
- Consent
- Contract
- Legal obligation
- Vital interest of the data subject
- Balance between interests of data holder & data subject
- Outlines key rights of individuals (data subjects):
- Right to access the data
- Right to know the data’s source
- Right to correct inaccurate data
- Right to withhold consent to process data in some situations
- Right of legal action should these rights be violated
- Even organisations outside Europe must consider these rules due to trans-border data flow requirements
- US businesses doing business in Europe can obtain protection under the Privacy Shield agreement between the EU and the US that allows the Department of Commerce & the Federal Trade Commission (FTC) to certify businesses that comply with regulations
- Replaces the invalidated “safe harbor” agreement between the US and the EU
- Privacy Shield requirements [EXAM]
- Notice: Inform individuals about the purpose for which data is collected & used.
- Choice: Offer an opportunity to opt out.
- Security: Take reasonable precautions to protect data.
- Data Integrity & Purpose Limitation: Only collect data that is needed for processing purposes identified in the Notice. Take reasonable steps to ensure that personal data is accurate, complete & current.
- Access: Individuals mist have access to their data, and the ability to correct, amend or delete when inaccurate.
- Recourse, Enforcement & Liability: Implement mechanisms to ensure compliance with the principles and provide means to handle individual complaints.
- There is also a Swiss-US Privacy Shield
- Both programs are administered by the US Department of Commerce and organisations can self-certify by means of a lengthy questionnaire.
- Processing of data must meet one of the following criteria:
- GDPR
- Replaces EU DPD
- Now applies to all organisations who collect data from residents in the EU (or process information on their behalf)
- Some key provisions include:
- Breaches to be informed within 24 hours
- Centralised data protection authorities
- Individuals have the right to access their own data
- Data portability between service providers
- Right to be forgotten
- Companies that violate GDPR privacy rules are liable for fines of up to 4% of global revenue
- Encryption, pseudonymisation & anonymisation can reduce or remove the requirements of GDPR
- Pseudonymisation is similar to tokenisation, and involves replacing personal data (such as names) with artificial identifiers. These identifiers point to the real data held in a different location, so the process is reversible.
- Anonymisation, if done effectively, means that GDPR no longer applies, however data is difficult to truly anonymise and protect from data inference techniques.
- Consider a database containing a table of actors, a table of films, and a table of payments for each actor. These are linked, so you can see which actors appeared in which films, and how much each actor was paid.
- You could anonymise the actors table to remove the actor’s names, but it’s still relatively easy to identify the actors by the set of films they have appeared in, which is generally unique.
- Masking can be an effective way of anonymising data by swapping data in individual data columns, so that aggregated calculations can still be performed (e.g. average age) and the data still looks like real data, but doesn’t match reality.
- A very simple example of a table containing three fields – first name, last name and age, containing Joe Smith (25), Sally Jones (28), Bob Johnson (37) and Maria Doe (26) could become Sally Doe (37), Maria Johnson (25), Bob Smith (28) and Joe Jones (26).
- Unlike pseudonymisation/tokenisation, masking is irreversible.
- Wassenaar Arrangement – import/export controls for strong encryption
- Fourth Amendment (searching private property without warrant)
- Privacy Act (1974) – severely limits the way federal govt may deal with private information about individuals; agencies must maintain only the records necessary for conducting their business and destroy them when no longer needed; provides formal procedure for citizens to view their records and request that they be amended if incorrect; applies only to govt agencies
- Electronic Communication Privacy Act (ECPA, 1986)
- crime to invade electronic privacy of an individual
- broadened Federal Wiretap Act to apply to any illegal interception of electronic communicates or intentional unauthorised access to data
- monitoring mobile phone conversations is illegal and punishable by a fine up to $500 and imprisonment of up to 5 years
- Communications Assistance for Law Enforcement (1994, CALEA)
- requires all comms carriers to make wiretaps possible for law enforcement, with an appropriate court order, and regardless of the technology in use
- Economic Espionage Act (1996)
- extends definition of property to include proprietary economic info so the theft of such information can be considered industrial or corporate espionage
- Economic & Protection of Proprietary Information Act (EPPIA, 1996) – theft of economic information considered espionage
- US PATRIOT Act (2001) – provides blanket approval for surveillance (brought in after 9/11, aimed at terrorist activity)
- allows ISPs to provide information voluntary, as well as under subpoena
- amends CFAA to provide more severe penalties for criminal acts, with jail terms up to 20 yrs
- Identity Theft & Assumption Deterrence Act (1998)
- Makes identity theft a crime against the victim and provides severe criminal penalties of up to a 15-yr prison term and/or $250K fine
“Reasonable expectation of privacy”
- The US courts have maintained that the right to privacy (as an extension of the basic constitutional rights) should only be guaranteed where there is a reasonable expectation of privacy; for example, if you mail a letter in a sealed envelope, you may reasonably expect that it will be delivered without being read on the way – if you send a message on a postcard instead, you do so with the awareness that one or more people might read the message before it arrives at the other end
- Recent court rulings have found that employees do not have a reasonable expectation of privacy when using employer-owned equipment in the workplace, however if you’re planning to monitor employee communications, you should take reasonable precautions such as:
- Clauses in employment contracts that state that the employee should have no expectation of privacy while using corporate equipment
- Similar written statements in corporate acceptable use & privacy policies
- Logon banners warning that all communications are subject to monitoring
- Labels on computers & telephones warning of monitoring
Intellectual Property
- Copyright: Lasts until 70 years after author’s death (95 years from date of publication for anonymous works, or works for hire; or 120 years from date of creation, whichever is shorter)
- Can be officially registered, but not necessary as protection is automatic
- DMCA protects copy-protection mechanisms and brings US in line with WIPO treaties; limits liability of ISPs but they must promptly remove stored content when notified of infringement
- Trademarks: 10 years, then renewed for 10 years at a time
- Should not be purely descriptive, or confusingly similar to another trademark
- Patents: 20 years from application date (Patent Application: TEN times Two) then expires and anyone can use the idea
- Inventions should be new, useful and non-obvious
- Trade secret: Indefinite (organisation must implement own controls)
- Can be formally protected by copyright or patents, but this will reveal the secret!
- NDAs etc
- One of the best ways to protect computer software
- Economic Espionage Act (1996) made it illegal to steal trade secrets from a US corporation with the intent of benefitting a foreign government or agent (up to $500K fine and up to 15 years imprisonment); theft of trade secrets under other circumstances is up to $200K and 10 years – companies must be able to prove that their trade secrets are well protected.
Compliance
- PCI DSS is an example of a compliance requirement that is not dictated by law, but by contractual obligation (via a merchant agreement between a business accepting credit cards and the bank that processes the transactions)
- It has 12 main requirements:
- Install & maintain firewall to protect cardholder data
- Do not use default values for passwords & other security parameters
- Protect stored cardholder data
- Encrypt transmission of cardholder data across open networks
- Protect all systems against malware; regularly update AV software
- Develop & maintain secure systems & applications
- Restrict access to cardholder data by need-to-know
- Identify & authenticate access to system components
- Restricted physical access to cardholder data
- Track & monitor all access to network resources & cardholder data
- Regularly test security systems & processes
- Maintain a policy that addresses info sec for all personnel
- Also applies to organisations that are not merchants, but store, process or transmit credit card information on behalf of merchants, such as shared hosting providers
- It has 12 main requirements:
- SOX (Sarbanes-Oxley Act) is an example of a regulation which requires security controls around financial systems
- Organisations may be subject to compliance audits, either by their existing internal & external auditors or by regulators
Third-party governance
- Mandated on you by law, regulation, industry standard, contractual obligation etc; generally involves outside investigator/auditor
- Another aspect is the application of security oversight on third-parties on which you rely
- Documentation review – reading exchanged materials (e.g. third party policy & reports) and verifying them against standards & expectations (typically before any on-site inspection)
- If documentation is not in compliance, chances are the location is not either
- In many situations (commonly government/military) failure to provide sufficient documentation can result in loss of authorisation to operate (ATO), requiring a complete document review & on-site review to re-establish
- If documentation is complete & sufficient, existing ATO can be maintained, or temporary ATO (TATO) can be granted
- Questions to cover during vendor governance reviews:
- What types of sensitive info are stored, processed or transmitted?
- What controls are in place to protect information?
- How is our organisation’s information segregated from that of other clients?
- If applicable, what encryption algorithms & key lengths are used, and how is key management handled?
- What type of audits does the vendor perform, and does the client have access to the reports?
- Does the vendor rely on any third-parties to store, process or transmit data? How to the security provisions of the contract extend to these parties?
- Where will data storage, processing & transmission take place? If outside the home country of the client/vendor, what are the implications?
- What is the vendors incident response process, and when will clients be notified of a potential breach?
- What provisions are in place to ensure the ongoing integrity & availability of client data?
Personnel security
- Job rotation provides knowledge redundancy as well as reducing risk of fraud etc. Cross-training involves preparing workers to perform other job positions, but not actually rotating jobs unless needed to fill a work gap, e.g. as part of an emergency response
- Training is considered an administrative control.
- Mandatory vacations are a primarily detective control.
- Non-compete agreements are difficult to enforce legally but may still provide a deterrent for workers
- Primary purpose of the exit interview is to review any liabilities/restrictions placed on the former employee (most commonly an NDA)
Risk terminology
- Asset
- Asset Valuation
- $ value
- Threat
- any potential occurrence that may cause an undesirable outcome
- can result from action or inaction
- threat agents (usually people) intentionally exploit vulnerabilities
- threat events are accidental or intentional exploitations of vulnerabilities (natural or man-made)
- a realised threat is a threat that results in loss
- Vulnerability
- weakness in an asset, or the absence of a safeguard
- Exposure
- the potential of asset loss because of a threat
- experienced exposure means that a realised threat is actually occurring
- exposure factor (EF) is derived from this concept
- Risk
- the likelihood that at a threat will exploit a vulnerability to cause harm to an asset
- as a formula: risk = threat * vulnerability
- Safeguards
- the only means by which a risk is mitigated
- reconfiguring existing security and even removing elements from the infrastructure are valid safeguards – not just purchasing new tools
- Attack
- deliberate exploitation of a vulnerability by a threat agent
- can also be viewed as any violation of an organisation’s security policy
- Breach
- the occurrence of a security mechanism being bypassed by a threat agent
Remember:
Threats exploit vulnerabilities which results in exposure.
Exposure causes risk.
Risk is mitigated by safeguards which protect assets (which are endangered by threats).
Risk analysis
- Quantitative or qualitative – usually both (i.e. hybrid)
- Major elements of a quantitative RA:
- Assign asset value (AV)
- Calculate exposure factor (EF)
- Calculate single loss expectancy (SLE)
- Assess the annualised rate of occurrence (ARO)
- Derive the annualised loss expectancy (ALE)
- Perform cost/benefit analysis of countermeasures
- EF represents %age loss of an asset from a realised risk (loss potential)
- SLE = AV * EF
- ALE = SLE * ARO (or ALE = AV * EF * ARO)
- Cost/benefit analysis: (ALE1 – ALE2) – ACS
- ALE1: ALE before safeguard
- ALE2: ALE after safeguard
- ACS: annual cost of safeguard
- Delphi technique (used in qualitative RA): anonymous feedback-and-response process used to enable a group to reach a consensus.
- Countermeasure selection is not part of risk analysis – it’s a later activity of the wider risk management piece
- Total risk is the amount of risk an organisation would face if no safeguards were implemented:
threats * vulnerabilities * asset value = total risk
(In this case, * implies a combination function, not multiplication – it’s not a true mathemetical formula) - Controls gap: difference between total & residual risk (i.e. the amount of risk that is reduced by implementing controls:
total risk – controls gap = residual risk - Recovery controls are a more advanced extension of corrective controls; examples include backups, fault-tolerant RAID, AV software, DB shadowing etc.
- Specialist software is a good way to reduce the burden on risk analysis staff, particularly on quantitative analysis.
Risk management frameworks
- NIST Risk Management Framework (RMF)
- Defined in SP 800-37
- Lists 6 steps (CSIAAM):
- Categorise the information system
- Select baseline controls
- Implement controls
- Assess controls
- Authorise information system operation
- Monitor the controls in the information system (ongoing)
- Other RM frameworks include:
- OCTAVE (Operationally Critical Threat, Asset & Vulnerability Evaluation)
- FAIR (Factor Analysis of Information Risk)
- TARA (Threat Agent Risk Assessment)
Domain 2: Asset Security
Assets include sensitive data, the hardware used to process it, and the media used to hold it.
Two areas where organisations typically trip up:
- Backup media should be protected with the same level of protection as the data that is backed up!
- Properly sanitising media and/or equipment when it is at the end of its lifecycle
Record retention: A good reason to define a record retention policy is to prevent unnecessary legal issues, such as having to trawl through old emails which could/should have been deleted. A company cannot legally delete potential evidence after a lawsuit is filed, however if a record retention policy is in place, it is legal to delete data older than the maximum retention period before any lawsuit is filed.
Hardware retention: Keeping hold of hardware until it has been properly sanitised
Personnel retention: In this context, refers to knowledge that staff gain while being employed by an organisation. NDAs are widely used to prevent current or former employees from sharing proprietary data.
Methods of removing data
- Erasing: Simple logical deletion of file – data is still there
- Clearing: Overwriting. Can be recovered in some labs using specialist tools. Suitable only for unclassified data
- Purging: Intense form of clearing. Press media for use in a less sensitive environment. Data is non-recoverable using known methods. Not suitable for highly classified data (e.g. Top Secret).
- Declassification: Process of using media in an unclassified environment.
- Sanitisation: Combination of processes to remove data, ensuring data cannot be recovered at any cost. Usually stops short of physical destruction.
- Destruction: Final stage in media lifecycle. Most secure option. Can include shredding, incineration, dissolving with chemicals etc. Often cheaper to destroy & purchase new media than have assured sanitisation, and no risk of a new method of data recovery being discovered. Only truly secure method for SSD sanitisation.
- Good idea to encrypt all data on SSDs, so any data that manages to escape the sanitisation process cannot be read.
- Note on degaussing: Good for magnetic tapes, not recommended for hard drives; the strong magnetic field usually destroys the sensitive electronics used to read the data, leaving you with no way of verifying whether the data has been destroyed. Someone could open the drive in a cleanroom and transplant the platters to another drive in order to read the data.
Data roles
- Business/Mission Owner: Has responsibility for a department, e.g. sales dept. Owns the process and is responsible for ensuring it provides value to the organisation. IT governance models such as COBIT are sometimes used to help business owners balance security control requirements with business or system need, and justify the cost of security to the business.
- System Owner: Person responsible for actual computers that house data, including their hardware/software config. Develops system security plan and ensure it is deployed. Delegates technical responsibilities to custodians.
- Data Owner: Ultimately responsible for data. Classifies the data and specifies controls. Management duties rather than hands-on. Typically CEO, president or dept head. Business, System and/or Data Owner roles can be combined
- Data Administrator: Grants access to personnel as directed by data owner, typically using RBAC (assigning/deassigning users to roles).
- Custodian: Performs hands-on tasks to protect assets as directed by data owner/system owner (e.g. making backups). Process followers, not decision makers.
- Data Controller: Person who controls processing of data (e.g. HR/payroll dept)
- Data Processor: Entity who processes personal data on behalf of a data controller (e.g. third-party payroll company). Must protect the privacy of the data and not use it for any purpose other than directed by the data controller.
“Rules of behaviour” are established by the Data Owner and are effectively the same as an acceptable use policy (AUP). These outline the responsibilities & expected behaviour of individuals, and state the consequences of non-compliance.
Certification & accreditation
- Certification means a system has been certified to meet the security requirements of the data owner. You can be CERTain that it meets its requirements!
- Certification considers the system, the security measures taken to protect it, and the residual risk represented by it.
- Accreditation is the data owner’s formal acceptance of the certification and of the residual risk, which is required before the system is put into production. The data owner believes the system is CREDible!
Standards & control frameworks
PCI DSS
- Industry specific: applies to vendors who store, process and/or transmit payment card data
- Created by the Payment Card Industry Security Standards Council, comprised of AmEx, Discover, MasterCard, Visa and other.
- Seeks to protect credit card data by requiring vendors to take specific precautions
- Based on a set of core principles:
- Build & maintain a secure network, and systems
- Protect cardholder data
- Maintain a vulnerability management program
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain an information security policy
- Vendors must either carry out regular web vulnerability scans, or place their applications behind a web application firewall
OCTAVE
- Stands for Operationally Critical Threat, Asset & Vulnerability Evaluation
- A risk management framework from Carnegie Mellon University
- Describes a three-phase process for managing risk:
- Phase 1 identifies staff knowledge, assets & threats
- Phase 2 identifies vulnerabilities and evaluates safeguards
- Phase 3 conducts the risk analysis & develops the risk mitigation strategy
Common Criteria
- International standard for describing and testing the security of IT products
- Presents a hierarchy of requirements for a range of classifications & systems
- Key terms:
- Target of evaluation (ToE): The system or product that is being evaluated
- Security target (ST): The documentation describing the ToE, including the security requirements and operation environment
- Protection profile (PP): An independent set of security requirements & objectives for a specific category of products/systems, such as firewalls or IDSs
- Evaluation assurance level (EAL): The evaluation score of the tested product or system. There are seven EALs, each building upon the previous level (for example, EAL3 products can be expected to meet or exceed the requirements of products rated EAL1 or EAL2):
- EAL1: Functionally tested
- EAL2: Structurally tested
- EAL3: Methodically tested & checked
- EAL4: Methodically designed, tested & reviewed
- EAL5: Semi-formally designed & tested
- EAL6: Semi-formally verified, designed & tested
- EAL7: Formally verified, designed & tested
The ISO 27000 series
- ISO 27002 is a set of optional guidelines for an information security code of practice. It was based on BS 7799 Part 1 and was renumbered from ISO 17799 in 2005 for consistency with other ISO security standards. It has 11 areas, each focusing on specific info sec controls:
- Policy
- Organisation of info sec
- Asset management
- HR security
- Physical & environmental security
- Comms & operations management
- Access control
- Information systems acquisition, development & maintenance
- Info sec incident management
- Business continuity management
- Compliance
- ISO 27001 is a related standard and comprises mandatory requirements for organisations wishing to be certified against it
COBIT
- A control framework for employing info sec governance best practices within an organisation
- Developed by ISACA (Information Systems Audit & Control Association)
- Made up of four domains:
- Plan & Organise
- Acquire & Implement
- Deliver & Support
- Monitor & Evaluate
- Key principles include:
- Meeting stakeholder needs
- Covering the enterprise end-to-end
- Applying a single, integrated framework
- Enabling a holistic approach
- Separating governance from management
ITIL
- Information Technology Infrastructure Library
- A framework for providing best practice in IT Service Management
- Contains five core publications providing guidance on various service management practices:
- Service Strategy: helps IT provide services
- Service Design: details the infrastructure & architecture required to deliver IT services
- Service Transition: describes taking new projects and making them operational
- Service Operation: covers IT operations controls
- Continual Service Improvement: describes ways to improve existing IT services
Scoping & tailoring
- Scoping is the process of determining which parts of a standard/baseline should apply to an organisation. For example, an organisation that does not employ wireless equipment may declare the wireless provisions of a particular standard are out of scope and therefore do not apply.
- Tailoring is the process of customising a standard for an organisation to align with its mission. It begins with controls selection, continues with scoping & finishes with the application of compensating controls.
US government organisations are required to comply with many of the standards published in NIST SP-800 documents. These same documents are used by many private sector organisations to develop & implement their own security standards.
Cryptography, cryptanalysis & cryptography
- Cryptography is the art of creating & implementing secret codes & ciphers.
- Cryptanalysis is the study of methods to defeat codes & ciphers.
- Together, cryptography & cryptanalysis are referred to as cryptology
Symmetric vs asymmetric encryption
- Symmetric = secret key or private key cryptosystems using a single shared key (shared secret)
- Asymmetric = public key cryptosystems, using pairs of public and private keys
Other terms
- Initialisation vector (IV or nonce) used to create unique ciphertext each time the same message is encrypted using the same key
- Split knowledge and M of N control can be used for key escrow
- Work function or work factor (time/cost effort to perform a brute-force attack) need only be slightly greater than the time value of the asset (e.g. if data only useful for 10 years, an 11-year work factor is sufficient) – principle that all security, including crypto, should be cost effective & cost efficient; provide sufficient protection without unnecessary effort.
- Codes do not always provide secrecy; e.g. the “10-system” used by law enforcement is commonly known by the public, but it does provide for ease of communication.
- All ciphers provide secrecy, and are always meant to hide the true meaning of a message.
- Remember that codes work on words & phrases, whereas ciphers work on individual characters & bits
Substitution cipher
- Caesar cipher (ROT3) is an example of a shift cipher, which shifts each letter three places to the right to encrypt (and three places to the left to decrypt) – vulnerable to frequency analysis
- Polyalphabetic ciphers like Vigenère not vulnerable to direct frequency analysis, but to a second-order form of frequency analysis called period analysis
- One-time pads are a powerful form of polyalphabetic cipher which are considered unbreakable as long as the one-time pad (which must be as long as the message to be encrypted) is truly random, physically protected from disclosure, and only used once.
- Caesar shift cipher, Vigenère and one-time pads are very similar – the only difference is the key length. Caesar cipher uses a key of length one, Vigenère using a longer key (usually a word or sentence) and one-time pad uses a key as long as the message.
- Running key cipher uses a passage from a book or newspaper as the key. It assigns a numeric value to the plaintext and the key and performs modulo 26 addition to determine the ciphertext.
Transposition cipher
- Provides transposition, or permutation, by rearranging the character of the plain text (like an anagram)
- Columnar transposition numbers the letters in a keyword in alphabetical order and arranges the message underneath in columns. The columns are then read vertically in order of the numbers to encipher the message
Unsorted
Biba vs Bell-LaPadula
- Imagine the “i” in Biba means “integrity” – leaving Bell-LaPadula for confidentiality
- Bell-LaPadula is hard to write down! So this has the “no write down” rule
- “Written in the stars” applies to the write rules in both models
- *-Property in BLP (no write down)
- * Integrity Property in Biba (no write up)
Fire classes
(A)sh – Common combustibles: wood, paper
(B)oil – Liquid fires
(C)urrent – Electrical fires
(D)ent – Metal fires
(K)itchen
Fire extinguishing agents
Soda acid – reduces fuel intake
Halon (or equivalent) – reduces chemical reaction
CO2 – removes O2
Water – reduces heat
Database terminology
Relation = table
Attribute = column
Tuple = row
Cardinality = number of rows
Degree = number of columns
Domain = all possible values of a column
SW-CMM
IRDMO:
Initial – disorganised, no process
Repeatable – life cycle mgmt process introducts, project planning, QA etc
Defined – developers operate with formal procedure; more oganised
Managed – detailed understanding of development; quantitive development metrics & quality mgmt
Optimised – sophisticated dev process; feedback oriented; change mgmt
Composition theories
- Cascading
- Feedback
- Hookup
Waterfall is a SW dev methology, not a comp theory.
Iterative is not a comp theory.
Misc stuff
MAC addresses must be locally unique (in theory, they are globally unique, but this is not guaranteed)
Ring model only has 4 rings (0-3), rings 1 & 2 (device drivers) not normally implemented in practice; 0 = kernel, 3 = user.
TCP handshake: SYN > SYN/ACK > ACK
Turnstile is best way to restrict access into or out of a facility (one person at a time, often directional), not mantrap
Secondary verification mechanisms establish the correctness of detection systems
Governments tend to prioritise confidentiality, private companies often favour availability.
Operational Technology systems (PLCs, SCADA) tend to prefer availability, then integrity, then finally confidentiality – AIC triad.
MOM – Means, Opportunity & Motive: the three things an attacker/adversary needs
CIDR
WAF = reverse proxy
TOTP = Time-Based OTP (One-Time Passwords)
Rules of behaviour: Rules identified for the protection of data. RoB apply to the user, not the system.
Static RAM (SRAM) uses “flip-flops” (latches) – faster.
Dynamic RAM (DRAM) uses small capacitors – slower/cheaper.
Both types are volatile (lose data upon power loss) but DRAM requires constant refreshing while SRAM does not.
Quality Control (QC) – assessment of quality based on interernal standards
Quality Assurance (QA) – assessment of quality based on external standards; involves reviewing of QC processes & activities
DAM = Database Activity Monitoring
Data dispersion replicates data in multiple physical locations
Data fragmentation splits data into shards and distributes them across a large number of machines
Tokenisation replaces sensitive data (e.g. credit card numbers) with a reference to that data (that may reside elsewhere, e.g. in a more secure environment)
Some implementations of EMV payment cards use 3DES encryption.
Blowfish uses 32-448 bit key sizes and is used by bcrypt (Linux) to encrypt passwords. Bcrypt adds a 128-bit salt to protect against rainbow table attacks.
SSL is susceptible to POODLE (Padding Oracle On Downgraded Legacy Encryption) and should ideally be disabled in favour of a TLS-only approach.
IPSec is often combined with L2TP (Layer 2 Tunnelling Protocol) for VPNs. L2TP itself transmits data in cleartext, but is used with IPSec in tunnel mode to protect data in transit.
NOT: ~ or ! symbol
XOR: ⊕ (X within an O, Rotated) or ⊻ (OR with a line under it)
Modulus: mod or %
Tough Questions 61-70
- You are using an encryption scheme which generates seemingly random bits which are then XOR’d with the plaintext data in order to product ciphertext. Which type of algorithm is this?
(a) Stream cipher
(b) ECC
(c) Diffie-Hellman
(d) RSA
(e) Key stretching
(f) Block cipher
Answer:
(a)
- Your company is being a cloud migration and is planning on moving many of its existing apps and services. Which of the following will allow moving of the apps & services to the cloud while still providing control of the underlying OS on which the apps/services run?
(a) Platform as a Service
(b) Infrastructure as a Service
(c) Software as a Service
(d) Storage as a Service
Answer:
(b)
- Which of the following are reasons for implementing logon banners? (Choose three)
(a) Provide a welcome message to connecting users
(b) Notifying users of active monitoring
(c) Provide system information upon connection
(d) Deter hackers attempting to connect
(e) Establishing “no expectation of privacy”
(f) Definining who is allowed to access the system
Answers:
(b), (e), (f)
- Which of the following mechanisms provides the greatest capacity for individual accountability?
(a) Hashing files to ensure integrity
(b) Logging activity per IP address
(c) Setting permissions on folders
(d) Individual sign-on per user
(e) Limiting the number of employees that have keys to the building
Answer:
(d)
- In an effort to increase the security of SSH on your Linux server, you implement a technique that requires users to attempt connections to three seeimingly random ports before connecting to port 22. Which of the following terms best describes this technique?
(a) Firewalking
(b) Port mapping
(c) Port knocking
(d) Secret handshake
(e) Session triggering
(f) Kernel handshaking
Answer:
(c)
- Which of the following are NOT private IP addresses defined by RFC 1918? (Choose all that apply)
(a) 172.32.31.45
(b) 192.188.4.3
(c) 10.16.31.22
(d) 169.254.67.89
(e) 172.29.35.9
(f) 131.107.33.1
(g) 192.168.44.200
(h) 172.6.32.1
Answers:
(a), (b), (d), (f), (h)
- Which of the following are NOT characteristics of Kerberos? (Select all that apply)
(a) Uses symmetric keys to secure session tickets
(b) Provides for resource authorisation
(c) Creates capacity for Single Sign-On
(d) Leverages encrypted timestamps to mitigate reply attacks
(e) Public keys are used to secure the TGT
(f) Requires principal & server to trust KDC
Answers:
(b), (e)
Explanation:
(b) Kerberos provides authentication, not authorisation
(e) The TGT is secured with a symmetric secret
- Which of the following is true?
(a) An access control list (ACL) is a list of permissions associated with a subject
(b) Associated with an object, a capabilities list is a list of actions permitted to a given subject
(c) Removing a user from an object ACL will always prevent the user from accessing the object
(d) An access control list (ACL) is effectively a column in an access control matrix
(e) A capabilities table and an access control list are the same thing
Answer:
(d)
Explanation:
(b) is incorrect because a capabilities list is associated with a subject, not an object
- A user hashes a file using SHA1:
$ shasum -a 1 vacation.jpg bc54e52af85af1ca7f8c8526dc38182999914614 vacation.jpg
The user then makes a small change to the image, renames it and emails it to a friend.
If the friend were to hash the image received in the email, he would get:$ shasum -a 1 beachweek.jpg 1ad5b0215c0221f5463209c69fd9178e5657f3ab beachweek.jpg
Six months later, an investigator wants to determine if the ‘beachweek.jpg’ image is located on the original user’s computer.
Which of the following might help the investigate locate the original (and similar) ‘vacation.jpg’ image?
(a) Hash all the files using SHA-256 and look for a matching hash
(b) Look in the Sent items folder in the user’s email program
(c) Search for images of a similar size and file type
(d) Use a fuzzy hashing tool
(e) Create SHA1 hashes of each file and compare the last 8 bits of the hash value
Answer:
(d)
Explanation:
(d) Fuzzy hashing is a technique that looks for similarities in files, not by hashing the entire file, but by hashing the file in parts. When somebody makes a subtle change to a file, standard hashing algorithms would create a completely different hash, but fuzzy hashing divides the file into chunks/blocks and determines similarities between blocks to give you a “percentage likeness” – ssdeep is an example of a fushing hashing tool.
- You have just received a digitally signed email message. What do you need in order to validate the integrity & authenticity of the message?
(a) Your private key
(b) Sender’s private key
(c) Root CA’s private key
(d) Your public key
(e) Sender’s public key
(f) The passphrase for the message
Answer:
(e)
Tough Questions 51-60
- You have just learned that several of your developer’s notebooks are infected with information-stealing malware. The infection vector appears to be malicious banner ads on a third-party website populate with the developers in your business. Which of the following attacks has most likely occurred?
(a) Spear phishing
(b) Social engineering
(c) Watering hole
(d) Buffer overflow
(e) Rootkit
Answer:
(c)
Explanation:
A watering hole attack is a method of compromise in which malicious actors infect a website with malware that targets users accessing the website (e.g. by purchasing ad space on a popular website and using that ad space to spawn malicious code)
- You work for a small business that has implemented WPA-PSK for its WLAN. You want to defend against an attacker capturing the authentication exchange and attacking it offline. Your passphrase is currently 10 characters long and uses only upper- and lower-case letters. Which of the following will provide you the BEST defence against an offline attack?
(a) Switch from AES-128 to AES-256
(b) Leave the passphrase length at 10, but use lower-case, upper-case, numbers & special characters in the PSK
(c) Configure WPA-PSK to use bcrypt rather than PBKDF2
(d) Change to a 14-character passphrase while continuing to use just upper- and lower-case letters
(e) Use WPA2 rather than WPA version 1
(f) None of the above: the encryption keys are ephemeral, therefore the authentication is not attackable
Answer:
(d)
Explanation:
(b)/(d) A 14-character passphrase composed of only upper- and lower-case letters has higher entropy than a 10-character passphrase also including numbers & special characters (approx 78 bits vs 65 bits, which is many orders of magnitude greater)
(e) Everyone should be using WPA2, but upgrading from WPA1 to WPA2 won’t specifically solve the problem.
(f) The keys are ephemeral but this doesn’t mean the authentication is not attackable.
- Which of the following are not characteristics of Discretionary Access Control? (Choose three)
(a) Object access is based on sensitivity
(b) It is difficult & expensive to implement
(c) Object owner defines access rights
(d) Easy to administer & use
(e) It is closely aligned with Bell-LaPadula
(f) It is less restrictive than role-based access control (RBAC)
Answers:
(a), (b), (e)
- A race condition has been identified in a multi-threaded application running on your server. Which of the following is the common concern associated with this?
(a) Covert storage channels
(b) Covert timing channels
(c) Time-of- check/time-of-use (TOC/TOU) errors
(d) Polyinstantiation
(e) Buffer overflows
Answer:
(c)
- Which of the following are characteristics of the Brewer & Nash security model? (Choose three)
(a) No read up (Simple Security Rule)
(b) No write down (* Property Rule)
(c) Also called “Chinese Wall”
(d) Calls for dynamically-changing permissions
(e) Designed to prevent conflicts of interest
(f) No write up (* Integrity Axiom)
(g) No read down (Simple Integrity Axiom)
Answers:
(c), (d), (e)
- Which of the following methods of data removal will leave data remanence concerns? (Select all that apply)
(a) Holding Shift key while deleting a file in Windows
(b) Formatting a hard drive before selling it on eBay
(c) Using dd to overwrite a disk with random bits
(d) Using a crypto-shredding technique
(e) Degaussing
Answers:
(a), (b)
- Which of these is the best definition of a Recovery Point Objective (RPO)?
(a) Maximum amount of time a business process can be unavailable
(b) Maximum amount to time to recover a business process
(c) The amount of time need to verify a system/data after recovery
(d) Measure of time indicating the maximum amount of data that can be lost
Answer:
(d)
- Which of the following hashing algorithms produces output less than 200 bits?
(a) SHA2
(b) Whirlpool
(c) SHA1
(d) AES-CCMP
(e) RC5
(f) MD5
Answers:
(c), (f)
Explanation:
SHA2 is a collection of algorithms, but all produce hashes longer than 200 bits: SHA-224, SHA-256, SHA-384 etc. Whirlpool is 512-bit. SHA1 produces a 160-bit hash. MD5 is 128-bit. AES-CCMP & RC5 are not hashing algorithms.
- You are sending an email encrypted with a symmetric key. The symmetric key is encrypted using the recipient’s public key. What is the common term used to describe the encrypted message structure?
(a) Digital signature
(b) Hashed Message Authentication Code (HMAC)
(c) Message Integrity Check (MIC)
(d) Digital envelope
Answer:
(d)
Explanation:
(b) HMAC is simply hashing with a secret (such as a password) thrown into the mix to provide authentication as well as integrity
- Which of the following memory addressing types is used by programs on your system?
(a) Physical addressing
(b) Logical addressing
(c) Relative addressing
(d) Indirect addressing
Answer:
(b)
Explanation
(d) Some texts refer to “indirect addressing” which means the same as “logical addressing” (and “direct addressing” which means the same as “physical addressing”, so this could be a valid answer too.
Tough Questions 41-50
- Here are 10 different line items, seven (7) of which are part of the NIST recommended contingency planning (CP) process.
Select the seven that are part of the process, and organise them in order, from first to last:
(a) Create contingency strategies
(b) Develop an information system CP
(c) Identify misuse case scenarios
(d) Conduct a Business Impact Analysis (BIA)
(e) Develop software test procedures
(f) Ensure plan testing, training & exercises
(g) Assign a department head to lead development
(h) Identify preventive controls
(i) Develop a CP policy statement
(j) Maintain the CP plan
Answers:
(i), (d), (h), (a), (b), (f), (j)
Explanation:
1. The seven steps of the NIST-recommended CP process are, in order:
2. Develop a CP policy statement
3. Conduct a Business Impact Analysis (BIA)
4. Identify preventive controls
5. Develop an information system CP
6. Ensure plan testing, training & exercises
7. Maintain the CP plan
- Which of the following best describes a blackout?
(a) A short-term dip (sag) in voltage
(b) A prolonged drop in voltage (minutes or longer)
(c) A complete loss of power
(d) A prolonged excess of voltage
(e) A short-term increase in voltage
Answer:
(c)
- As part of the evidence collection process, an investigator opens a terminal on the suspect machine and issues commands to display the current network settings, ARP cache, resolver cache & routing table. As each is displayed on the screen, he uses his mobile phone to take pictures of the data. Which of the following is true regarding his actions?
(a) By viewing the data, disclosure rules have been violated
(b) Running commands on the system has altered the system
(c) Chain of custody has been broken
(d) Photos of what is on a computer screen are not considered legally authentic
(e) Commands should only be executed through a remotely-established SSH connection
Answer:
(b)
- A developer in your company has written a script that changes a numeric value before it is read and used as a variable by another program. After the value is read, the developer’s malicious script changes the data value back to its original value. What is this an example of?
(a) Hacking
(b) Salami slicing
(c) Time of check/time of use (TOC/TOU) errors
(d) Polyinstantiation
(e) Data diddling
Answer:
(e) Data diddling
- Which of the following statements pertains to the Fourth Amendment of the the US Constitution?
(a) It established the rules of evidence for digital evidence collection
(b) It protects against the unlawful search & seizure by agents of the government
(c) It establishes the need for a private employer to obtain a warrant before investigating an employee
(d) It applies to public and private employers
Answers:
(b)
Explanation:
(c) & (d) The Fourth Amendment applies to agents of the government, not to private employers
- If Risk was a mathematical equation, what would it be?
(a) (Exposure * Impact) / Likelihood
(b) Threat * Vulnerability * Impact (or Cost)
(c) SLE * ARO
(d) Asset Value / (Threat * Likelihood)
(e) (Asset Value * Threat * Impact) / SLE
Answer:
(b)
- You have deployed a web application that allows your customers to view their private account information. You want to minimise the chances that an attacker within radio range of the customer’s wireless LAN (WLAN) will be able to eavesdrop on their traffic and intercept their private data. Which of the following is the best approach you can take to do this?
(a) Require SSH for all connections to the web server
(b) Implement TLS on the web server
(c) Advise your customers to deploy WPA2 with AES on their wireless LANs
(d) Digitally sign all traffic using RSA keys
(e) Require customers to connect via an IPsec VPN
(f) Implement 802.1x on your switches and provide steps for your customers to do the same
(g) Use an IDS (or IPS) to monitor for evidence of ARP flooding attacks
Answer:
(b)
Explanation:
TLS provides end-to-end encryption. (c) is out of your control and you can’t easily verify it’s been done, so (b) is the better answer. (e) would introduce unnecessary complexity.
- Examine the following IP packet. What type of attack is it?
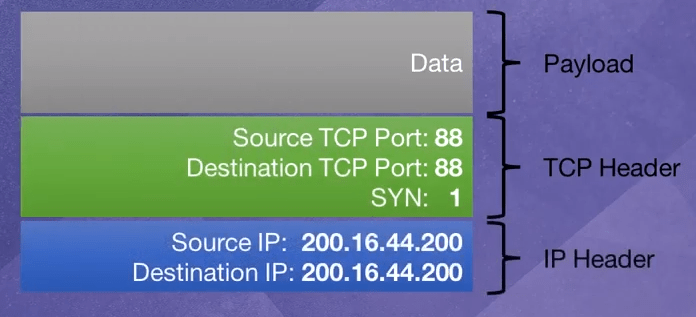
(a) TCP SYN flood
(b) Fraggle
(c) LAND
(d) Teardrop
(e) MITM
Answer:
(c)
Explanation:
A LAND (local area network denial) works by sending a packet to the victim,
where the source & destination IP addresses are the victim’s IP address, and
the source & destination ports are the same, with the aim of creating a loop
where the victim machine keeps responding to itself and eventually crashes.
- Which of the following is the best definition for circumstantial evidence?
(a) A reproduction of the original offered as proof
(b) Testimony from an individual who saw an event take place
(c) An original object offered as proof of a fact
(d) Evidence offered by one who learned it from another
(e) Information that relies on inference to establish a fact
Answer:
(e)
- Determining Maximum Tolerable Downtime (MTD) is a critical component of which of these?
(a) Business Impact Analysis
(b) Risk Assessment
(c) Recovery Time Objectives
(d) Recovery Point Objectives
Answer:
(a) Step 1 of BIA is to identify critical systems (this is where MTD questions will be asked and subsequently answered), Step 2 is to identify resource requirements, Step 3 is identification of recovery priorities. (c) & (d) are part of the BIA, along with the MTD.
Tough Questions 31-40
- Crime Prevention Through Environmental Design (CPTED) seeks to deter criminal/inappropriate activity through techniques of environmental design. Which of the following are components of CPTED’s strategy? (Choose three)
(a) Natural access control
(b) End-user security awareness training
(c) Building code security reviews
(d) Community activism
(e) Natural territorial reinforcement
(f) Environmental inconveniences
(g) Natural surveillance
Answers:
(a), (e), (g)
Explanation:
(a) Natural access control endeavours to clearly delineate the difference between public & private areas, e.g. through landscaping as well as lighting, fencing etc.
(e) Natural territorial reinforcement tries to create a situation where people feel a sense of ownership of their physical environment, which makes them protective of that environment.
(g) Natural surveillance breeds the idea that if someone does something, they will be seen doing it.
There is also a fourth element to CPTED not listed here: maintenance & activity support. Well-maintained areas are less attractive to attackers, and more likely to be occupied by legitimate people.
- Fires are typically broken down into types identified by the fuels that start and/or support them. Which of the following is associated with fires caused by flammable liquids like gasoline, petroleum oil or propane?
(a) Class A
(b) Class B
(c) Class C
(d) Class D
(e) Class K
Answer:
(b)
Explanation:
(A)sh – common combustibles
(B)oil – flammable liquids
(C)urrent – electrical
(D)ent – metal
(K)itchen
- At what layer of the OSI model does IPsec operate?
(a) Physical
(b) Data Link
(c) Network
(d) Transport
(e) Session
(f) Presentation
(g) Application
Answer:
(c)
- For convenience & cost savings, you wish to connect two sites across the public Internet. Once connected, the users & resources at each site will be able to securly communicate with each other, unaware of the location of the resources they are accessing. Of the following options, which is the most appropriate way to allow multiple users/services this type of site-to-site access?
(a) An SSL VPN
(b) TLS-encrypted desktop sharing
(c) An IPsec VPN tunnel between the two sites
(d) A GRE tunnel from the firewall at each site
(e) VRF routing with a protocol that supports strong authentication
Answer:
(c)
Explanation:
(d) is possible but GRE does not provide any confidentiality services natively so does not meet the “seamlessly & securely” qualification
(e) is a distractor (VRF is about having multiple routing tables on a router) - Packet filtering firewalls have several limitations that make them less appropriate than more modern solutions when protecting internal resources from Internet threats. Which of the following are shortcomings of packet filtering firewalls? (choose two)
(a) They control access based on source IP address and cannot verify if the address is being spoofed
(b) They use reverse path forwarding lookups
(c) They are stateless
(d) They do not support logging packets that match firewall rules
(e) They are stateful
(f) They defend against TCP SYN floods, which reduces their effective throughput
Answers:
(a), (c)
Explanation:
(b) is a distractor – reverse path forwarding lookups relate to multicast, not firewalls
(c) stateless means that the firewall looks at each packet as a free-standing entity, and is the reason why (a) is also true – there is no context to decide whether a single packet has a spoofed source address or not.
- Which of the following services/protocols are UDP based? (choose six)
(a) HTTP
(b) RADIUS
(c) SMB
(d) IMAP4
(e) SNMP
(f) NTP
(g) TFTP
(h) DNS (name resolution)
(i) SMTP
(j) Secure LDAP
(k) BGP
(l) DHCP
Answers:
(b), (e), (f), (g), (h), (l)
Explanation:
(b) RADIUS typically operates on UDP ports 1812 & 1813 (alternatively 1645 & 1646)
(c) SMB uses TCP port 445
(d) IMAP uses TCP port 143 (or 993 with TLS)
(e) SNMP is normally UDP based, on port 161 (port 162 for SNMP traps) – can optionally run on TCP but UDP is much more common
(f) NTP uses UDP port 123
(g) TFTP starts communication on UDP port 69
(h) DNS operates most commonly on UDP port 53 for name resolution, and TCP port 53 for zone transfers
(i) SMTP operates on TCP port 25, or TCP ports 587/465 for SSL/TLS implementations
(j) TLS-based secure LDAP uses TCP port 636
(k) BGP operates on TCP port 179
(l) DHCP typically runs on UDP port 67
- In 2001, NIST selected a replacement for DES (the Data Encryption Standard). The new specification is specified in the Advanced Encryption Standard. It operates on 128-bit blocks of data with key lengths of 128, 192 or 256 bits. What is the name of the family of algorithms selected by NIST?
(a) Twofish
(b) Blowfish
(c) Serpent
(d) Whirlpool
(e) Rijndael
(f) RC6
(g) IDEA
(h) MARS
Answer:
(e)
Explanation:
(a) was one of the five AES finalists, symmetric algorithm operating on 128-bits blocks of data using 128, 192 or 256 bit keys, and is patent- & royalty-free
(b) operates on 64-bit blocks – not an AES finalist, but wildly popular and also patent- & royalty free
(c) second place AES finalist, same block & key size as Twofish & Rijndael – more secure but slower than Rijndael
(d) is actually a 512-bit hashing algorithm available in three versions, most modern implementations use v3
(f) RC6 was an AES finalist, same block & key size again – would have been royalty-free if selected as winner, but is now not necessarily so, so other royalty-free algorithms are generally preferred
(g) operates on 64-bit blocks using a 128-bit key – originally positioned as a replacement for DES, not particularly prominent these days
(h) also an AES contender, variable key size & 128-bits of data, not often seen
- Which of the following are valid implementations of 3DES? (choose two)
(a) DES-EEE: All 3 keys are unique. Key is effectively 168 bits in length.
(b) DES-EDE: Key1 = Key2. Key3 is unique from Key1. Key is effectively 112 bits in length.
(c) DES-EDE: Key1 = Key 3. Key2 is is unique from Key1. Key is effectively 112 bits in length.
(d) DES-EED: Key1 = Key2. Key3 is unique from Key1. Key is effectively 112 bits in length.
(e) DES-EEE: All 3 keys are the same. Key is effectively 168 bits in length.
Answer:
(a), (c)
Explanation:
(a) EEE means 3 round of encryption. Key is effectively 3*56 = 168 bits.
(b) EDE means encrypt-decrypt-encrypt. Uses the same encryption key (Key1 and Key3) and a different decryption key (Key2). Key is effectively 2*56 = 112 bits.
- IPv6 introduces lots of new rules for address structure. Which of the following addresses are valid destination IPv6 addresses used for sending data to another node or nodes on the Internet? (choose all that apply)
(a) fe80::46c9:db66:2002
(b) 2002:46a8:8:722:d740:9be1:6f61:d864
(c) fda7:4967:fe1c:1::200
(d) 2620:0000:1234:cfg9:afc4:1:a:1100
(e) 3000:2341:5621:1:a84c::23::1
(f) ff1e:40:2002:abcd:dead:beef:1:11ee
(g) ff02::5
Answers:
(b), (f)
Explanation:
(a) “fe” prefix denotes a link-local IPv6 address
(b) 2 is a globally-routable prefix (as well as 3) and has 8 16-bit blocks for a total of 128 bits, so is a valid routable IPv6 address
(c) “fd” prefix denotes an IP that is part of the “unique local” address space
(d) the “g” is not a valid hexadecimal (0-9, a-f) character!
(e) double-colon notation can only be used (to represent a run of zeroes) ONCE in an IPv6 address
(f) “ff” means a multicast address, followed by a “1” meaning a transient/temporary address, followed by an “e” meaning globally routable (question states “nodes” as well as “node”, so multicast addresses are allowed)
(g) “ff” means a multicast address, followed by a “0” meaning link-local (this particular address is reserved for OSPF router communication)
- You have been given a 2TB ATA hard drive that spins at 15,000 RPM. Your task is to erase the data it contains in such a way that the erased data cannot be recovered using readily available “keyboard recovery” tools. As a minimum, what must you do?
(a) Use a data purging tool
(b) Physically destroy the drive
(c) Use a data clearing tool
(d) Format the drive using a different file system than was previously used
Answer:
(c)
Explanation:
Purging is erasing a medium in such a way that the data cannot be recovered using advanced laboratory techniques. Clearing will erase the medium in such a way that standard data recovery tools will not be able to successfully retrieve the data. So in this case, clearing meets the minimum requirement.
Tough Questions 21-30
- Cryptography provides many different types of protections of information. When utilised correctly, which of the following represent thing that cryptography CAN do? (choose six)
(a) Detect if a spreadsheet has been changed in an unauthorised way
(b) Provide confidentiality for a Windows user accessing a Linux web server via a web browser
(c) Prevent a user from deleting a file they have no permissions to access
(d) Provide a high degree of assurance that a remote system is who it claims to be
(e) Recover data that was changed in an unauthorised manner
(f) Prevent a thief from adding a stolen hard drive to a different computer in order to access its data
(g) Check to make sure a script is unmodified before allowing it to be executed
(h) Reduce the effectiveness of ICMP-based Denial of Service (DoS)
(i) Prevent an authorised user from exfiltrating data from a protected network
(j) Assist with complying with regulatory data security requirements
Answers:
(a), (b), (d), (f), (g), (j)
- When making decisions about how to best secure user computers & servers, which of the following is the most important consideration?
(a) Security should not decrease the usability of the system
(b) Intangible risks should be mitigated first
(c) Should cover all regulatory requirements
(d) Cost must be managed and should make sense for the given risk
(e) All risk should be eliminated by mitigating mechanisms
Answer:
(d)
(a) is not achievable in most cases, any controls are going to reduce usability (or speed, convenience etc.) to some degree, even if neglible
(c) is too broad
(e) is generally not possible
- Which of the following are typically NOT allowed to pass outbound through a firewall that leads to the Internet? (choose five)
(a) HTTP
(b) FTP
(c) SNMP
(d) DNS
(e) EIGRP
(f) RADIUS
(g) OSPF
(h) SSH
(i) SMTP
(j) LDAP
Answers:
(c), (e), (f), (g), (j)
Caveats apply, e.g. you may only wish to allow SSH to/from specific hosts, and SMTP from authorised mail servers on your network, not all nodes, but these are the best answer. Note that (e) and (g) are interior routing protocols.
- Which of the following are characteristics of elliptic curve cryptography? (choose four)
(a) It is stronger than RSA using significantly smaller key lengths
(b) It has a large memory footprint
(c) It can help conserve battery life in mobile devices
(d) It has lower CPU overhead compared to RSA
(e) It is not supported by most modern web browsers
(f) ECC was introduced as an alternative to AES
(g) It can be used in a Diffie-Hellman key exchange
Answers:
(a), (c), (d), (g)
- PCI DSS is a mandated information security standard that applies to organisations that accept credit cards. The primary objectives of the standard are to protect credit card information & reduce fraud. The security requirements for compliance with PCI DSS allow merchants to only store & retain certain types of cardholder information. Of the items listed below, which ARE ALLOWED to be stored by a merchant? (Choose three)
(a) Cardholder’s PIN
(b) Cardholder’s account number in plain text
(c) Card expiration date
(d) Full magnetic stripe data
(e) CAV2/CVC2/CVV2/CID
(f) Cardholder’s name
(g) Cardholder’s account number in an unreadable (i.e. encrypted/truncated) format
(c), (f), (g)
- Which of the following would be considered an administrative control? (Choose three)
(a) Background checks
(b) Network firewall
(c) Audible alarms
(d) Security awareness training
(e) Security guards
(f) Risk management
(g) Encryption of personnel records
Answers:
(a), (d), (f)
- What is the risk to electrical equipment when humidity is too high? (Choose two)
(a) ESD (electrostatic discharge)
(b) Short circuits
(c) Crosstalk
(d) Corrosion
(e) Sediment build-up on connectors
(f) Overheating
(g) Unplanned system reset
Answers:
(b), (d)
Explanation:
(a) ESD is caused when humidity is too low!
- Which of the following is something a network-based IDS (intrusion detection system) CANNOT do? (choose six)
(a) Inspect encrypted traffic for evidence of attack
(b) Detect illegal variations in protocol rules
(c) Compensate for weak passwords
(d) Detect TCP or ICMP-based denial of service attacks
(e) Filter malicious attachments from email messages
(f) Rate-limit attack traffic to inhibit its effectiveness
(g) Detect malicious activity on local hosts
(h) Act as a log of evidence for a successful attack
(i) Remove need for human intervention
Answers:
(a), (c), (e), (f), (g), (i)
Explanation:
(a) NIDs cannot inspect encrypted traffic
- Which of these is true of an IP routing table? (choose four)
(a) It maps MAC addresses & destination IP addresses to remote networks
(b) It contains a list of destination IP networks
(c) It contains a mapping of IP addresses & services offered on TCP ports
(d) It is created automatically via SNMP exchanges between neighbouring routers
(e) Networks learned via OSPF or EIGRP are more trusted than standard static routes
(f) IPv6 and IPv4-enabled routers use two routing tables, one for each protocol
(g) Routers can route packets with encrypted payloads
(h) Routing protocols secure routing update packets using TLS
(i) Routing tables map IP addresses to MAC addresses
(j) Routing tables operate at the Network layer of the OSI model
Answers:
(b), (f), (g), (j)
Explanation:
(e) Static routes are usually much more trusted that learned routes
(g) Yes, the payload can be encrypted, as long as the IP header is unencrypted
- Which of the following are characteristics of RAID 1? (Choose two)
(a) Also called ‘striping’
(b) All parity data is spread across the included drives
(c) Only supported on SSDs
(d) All parity data is stored on a single drive
(e) Disk-level encryption is enabled by default and is independent of the file system
(f) Has a 1:1 drive ratio (100%)
(g) Provides dynamic data de-duplication
(h) Also called mirroring
(i) Has a 1:x drive ratio, where x is the total number of drives
(j) Fast write, slow read
(k) System can survive multiple drive failures
(l) Has a 1:2 drive ratio (50%)
Answers:
(f), (h)
Explanation:
(a) Striping is RAID 0
(b) & (d) RAID 1 does not use parity
(f) One drive + one mirror = 1:1
(k) System can only survive a single drive failure
Tough Questions 11-20
- Mobile devices place an emphasis on battery consumption and frequently have limited processing power. What type of encryption is best suited to devices such as this?
(a) RSA
(b) Diffie-Hellman
(c) EAP-TLS
(d) PEAP
(e) ECC
(f) AES
(g) Vernam ciphers
Answer:
(e) ECC
Explanation:
(a) RSA asymmetric encryption requires long keys and therefore has a high processing overhead
(b) Diffie-Hellman is used for key exchange, not encryption in its own right
(c) & (d) are not concerned with encryption per se
(e) Elliptic curve cryptography is as secure as RSA using much smaller keys (at least 12 times smaller), so the processing power required is minimal
(f) AES does not particularly lend itself to limited processing power scenarios
(g) Vernam ciphers are another name for onetime pads, but again not what we’re looking for in this question
- Designed by Bruce Schneier, Blowfish is an encryption algorithm originally designed as an alternative to DES. Which of the following are characteristics of Blowfish? (Choose four)
(a) Key sizes of 128, 192 & 256 bits
(b) Key sizes from 32-448 bits
(c) Symmetric
(d) Asymmetric
(e) Patented
(f) Un-patented & license-free
(g) Used in bcrypt
(h) Used in scrypt
Answers:
(b), (c), (f), (g)
Explanation:
(a) These are the key sizes associated with AES
(b) Yes – think of a fish blowing up from 32 to 448 bits!
- The storage room in your office is equipped with an electronic lock that is configured to fail secure. What does this mean?
(a) Electricity keeps the lock engaged. If the power goes out, the lock will disengage, allowing the door to open.
(b) There is no current flowing to the door. In an emergency, an electric current will lock the door.
(c) Electricity keeps the lock disengaged. If the power goes out, the lock will engage, locking the door
(d) The lock can be controlled from a central location and locked/unlocked remotely
(e) The emergency systems in the building will unlock the door in the event of an emergency
(f) The emergency systems in the building will lock the door in the event of an emergency
Answer:
(c)
Explanation:
Fail safe means “fail safe for people”, fail secure means “fail secure for your stuff”! In a fail safe lock, electricity locks the door, so a loss of power will unlock the door. In a fail secure lock, electricity keeps the door unlocked, and a loss of power will lock the door. Note that even a fail secure lock generally allows free egress, e.g. a way for someone inside the secure building/area to get out.
- Your fire alarm system is being upgraded and you are considering the best options. One of the requirements is automatic notification of the local fire department when there is an event. Which type of system will provide this functionality?
(a) Protected premises fire alarm system
(b) Central station fire alarm system
(c) Auxiliary fire alarm system
(d) Public fire alarm reporting system
(e) Municipal fire alarm system
(f) Combination fire alarm system
Answer:
(c)
Explanation:
(a) is a local system
(b) involves a third-party monitoring company, e.g. ADT, not the fire department directly
(c) is a local system plus an interface to local emergency services
(d) & (e) are similar to each other, i.e. alarm system for the municipality, not something that can be installed in a private building
(f) is still local, the combination aspect relates to interfacing CCTV, CO detectors etc into the fire system
- Which of the following statements best align with (ISC)2‘s code of ethics? (Choose four)
(a) Work to protect society, public trust & the infrastructure
(b) Avoid using the Internet as a test network; consider the potential outcomes of your actions
(c) Be honest, act responsibility & with the confines of the law
(d) Deliver your product on time, as defined & within the allowed budget
(e) Be decisive, confident & articulate when dealing with principals
(f) Safeguard your systems using a complement of administrative, technical & physical controls
(g) Be competent in what you do, and be diligent in the maintenance of that competence
(h) Seek, through your actions, to improve the profession of information security
Answers:
(a), (c), (g), (h)
- ISO/IEC 15408 is an international standard for computer security certification. It provides a set of requirements for security functionality of IT products during a security evaluation, with the goal of providing a level of assurance that the product/system performs in a certain way. What is the more common name for this standard?
(a) NIST
(b) RMF
(c) TCSEC
(d) ITSEC
(e) Common Criteria
(f) Certification & Accreditation
(g) PCI
(h) COBIT
Answer:
(e) Common Criteria
- TCP, the Transmission Control Protocol, is referred to as being a ‘connection-oriented’ protocol. This, in part, means that client & server must first establish a connection before transmitting any data. The connection setup process is referred to as the “3-Way Handshake”. Which of the following is the appropriate order & direction of packets sent during the handshake?
(a) SYN from server to client, SYN/ACK from client to server, ACK from server to client
(b) SYN from client to server, SYN/ACK from server to client, ACK from server to client
(c) SYN from client to server, SYN/ACK from server to client, ACK from client to server
(d) SYN from client to server, ACK from server to client, ACK/PSH from client to server
(e) SYN/PSH from client to server, ACK/PSH from server to client, ACK from client to server
Answer:
(c)
Explanation:
Client initiates connection by sending a SYN, server replies with a SYN/ACK, client sends an ACK.
- 802.11 wireless LANs (WLANs) are inherently half-duplex. Because of this, they must arbitrate the use of the medium in order to manage collisions with other nodes on the radio network. Which of the following mechanisms is used by 802.11 in order to accomplish this?
(a) WDM (Wave Division Multiplexing)
(b) CSMA/CD (Carrier Sense Multiple Access/Collision Detection)
(c) TDMA (Time Division Multiple Access)
(d) CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance)
(e) Different frequencies for transmission & receive functions
(f) Token passing
(g) Time slots
(h) PCM (Pulse Code Modulation)
Answer:
(d)
Explanation:
(a) is used for fibre transmissions, (b) for early Ethernet, (c) for mobile phones, (h) is used for digital audio/telephony
- DDL, the Data Definition Language, is a standard for commands used to create the different structures in a database. The commands are used to create, modify or delete objects in a database. It is also used to create the logical structure of the database, including the definitions of all the objects & attributes in the database and their relationships to each other. What is the term used to describe this logical database structure?
(a) DCL
(b) Schema
(c) Normalisation
(d) Polyinstantiation
(e) Cardinality
(f) Relational
(g) SQL (Structured Query Language)
(h) DML
(i) AJAX
Answer:
(b)
Explanation
(a) DCL (Data Control Language) is associated with commits & rollbacks etc.
- In addition to IP addresses, DHCP servers provide network nodes with additional useful information such as a DNS server address, default gateway, and NetBIOS node type. Which of the following is NOT a legitimate attack that may be executed against your DHCP deployment? (Choose three)
(a) A rogue DHCP server on your network can offer IP addresses to legitimate users, thereby creating a DoS or MitM Situation
(b) An attacker may gain control of your DHCP server and reconfigure the options assigned to your clients
(c) Using TCP redirect messages, an attacker can send client DHCP packets to a remote DHCP server
(d) A rogue DHCP server can be used to reconfigure SMTP connection settings for internal email systems
(e) An attacker can request multiple IP addresses from the legitimate DHCP server, exhausting the available pool of addresses
(f) An attacker can remotely send negative acknowledgements whenever a client attempts to renew an IP address
Answer:
(c), (d), (f)
Explanation:
(c) for various reasons, not least that DHCP is UDP based