- Here are 10 different line items, seven (7) of which are part of the NIST recommended contingency planning (CP) process.
Select the seven that are part of the process, and organise them in order, from first to last:
(a) Create contingency strategies
(b) Develop an information system CP
(c) Identify misuse case scenarios
(d) Conduct a Business Impact Analysis (BIA)
(e) Develop software test procedures
(f) Ensure plan testing, training & exercises
(g) Assign a department head to lead development
(h) Identify preventive controls
(i) Develop a CP policy statement
(j) Maintain the CP plan
Answers:
(i), (d), (h), (a), (b), (f), (j)
Explanation:
1. The seven steps of the NIST-recommended CP process are, in order:
2. Develop a CP policy statement
3. Conduct a Business Impact Analysis (BIA)
4. Identify preventive controls
5. Develop an information system CP
6. Ensure plan testing, training & exercises
7. Maintain the CP plan
- Which of the following best describes a blackout?
(a) A short-term dip (sag) in voltage
(b) A prolonged drop in voltage (minutes or longer)
(c) A complete loss of power
(d) A prolonged excess of voltage
(e) A short-term increase in voltage
Answer:
(c)
- As part of the evidence collection process, an investigator opens a terminal on the suspect machine and issues commands to display the current network settings, ARP cache, resolver cache & routing table. As each is displayed on the screen, he uses his mobile phone to take pictures of the data. Which of the following is true regarding his actions?
(a) By viewing the data, disclosure rules have been violated
(b) Running commands on the system has altered the system
(c) Chain of custody has been broken
(d) Photos of what is on a computer screen are not considered legally authentic
(e) Commands should only be executed through a remotely-established SSH connection
Answer:
(b)
- A developer in your company has written a script that changes a numeric value before it is read and used as a variable by another program. After the value is read, the developer’s malicious script changes the data value back to its original value. What is this an example of?
(a) Hacking
(b) Salami slicing
(c) Time of check/time of use (TOC/TOU) errors
(d) Polyinstantiation
(e) Data diddling
Answer:
(e) Data diddling
- Which of the following statements pertains to the Fourth Amendment of the the US Constitution?
(a) It established the rules of evidence for digital evidence collection
(b) It protects against the unlawful search & seizure by agents of the government
(c) It establishes the need for a private employer to obtain a warrant before investigating an employee
(d) It applies to public and private employers
Answers:
(b)
Explanation:
(c) & (d) The Fourth Amendment applies to agents of the government, not to private employers
- If Risk was a mathematical equation, what would it be?
(a) (Exposure * Impact) / Likelihood
(b) Threat * Vulnerability * Impact (or Cost)
(c) SLE * ARO
(d) Asset Value / (Threat * Likelihood)
(e) (Asset Value * Threat * Impact) / SLE
Answer:
(b)
- You have deployed a web application that allows your customers to view their private account information. You want to minimise the chances that an attacker within radio range of the customer’s wireless LAN (WLAN) will be able to eavesdrop on their traffic and intercept their private data. Which of the following is the best approach you can take to do this?
(a) Require SSH for all connections to the web server
(b) Implement TLS on the web server
(c) Advise your customers to deploy WPA2 with AES on their wireless LANs
(d) Digitally sign all traffic using RSA keys
(e) Require customers to connect via an IPsec VPN
(f) Implement 802.1x on your switches and provide steps for your customers to do the same
(g) Use an IDS (or IPS) to monitor for evidence of ARP flooding attacks
Answer:
(b)
Explanation:
TLS provides end-to-end encryption. (c) is out of your control and you can’t easily verify it’s been done, so (b) is the better answer. (e) would introduce unnecessary complexity.
- Examine the following IP packet. What type of attack is it?
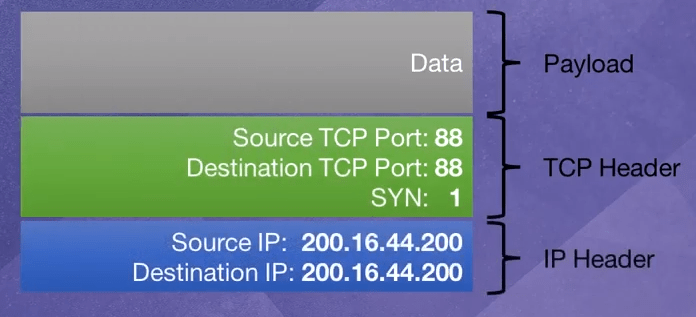
(a) TCP SYN flood
(b) Fraggle
(c) LAND
(d) Teardrop
(e) MITM
Answer:
(c)
Explanation:
A LAND (local area network denial) works by sending a packet to the victim,
where the source & destination IP addresses are the victim’s IP address, and
the source & destination ports are the same, with the aim of creating a loop
where the victim machine keeps responding to itself and eventually crashes.
- Which of the following is the best definition for circumstantial evidence?
(a) A reproduction of the original offered as proof
(b) Testimony from an individual who saw an event take place
(c) An original object offered as proof of a fact
(d) Evidence offered by one who learned it from another
(e) Information that relies on inference to establish a fact
Answer:
(e)
- Determining Maximum Tolerable Downtime (MTD) is a critical component of which of these?
(a) Business Impact Analysis
(b) Risk Assessment
(c) Recovery Time Objectives
(d) Recovery Point Objectives
Answer:
(a) Step 1 of BIA is to identify critical systems (this is where MTD questions will be asked and subsequently answered), Step 2 is to identify resource requirements, Step 3 is identification of recovery priorities. (c) & (d) are part of the BIA, along with the MTD.