- Which of the following is true for digital signatures?
(a) The sender encrypts the hash with a public key
(b) The sender encrypts the hash with a private key
(c) The sender encrypts the plaintext with a public key
(d) The sender encrypts the plaintext with a private key - Under which type of cloud service level would Linux hosting be offered?
(a) IaaS
(b) IDaaS
(c) PaaS
(d) SaaS - A criminal deduces that an organisation is holding an offsite meeting and there are few people in the building, based on the low traffic volume to and from the car park. The criminal uses the opportunity to break into the building and steal laptops. What type of attack has been launched?
(a) Aggregation
(b) Emanations
(c) Inference
(d) Maintenance Hook - EMI issues such as crosstalk primarily impact which aspect of security?
(a) Confidentiality
(b) Integrity
(c) Availability
(d) Authentication - You receive the following signed email from Roy. You determine that the email is not authentic, or it has changed since it was sent. In the diagram below, dentify the locally-generated message digest that proves the email lacks non-repudiation.
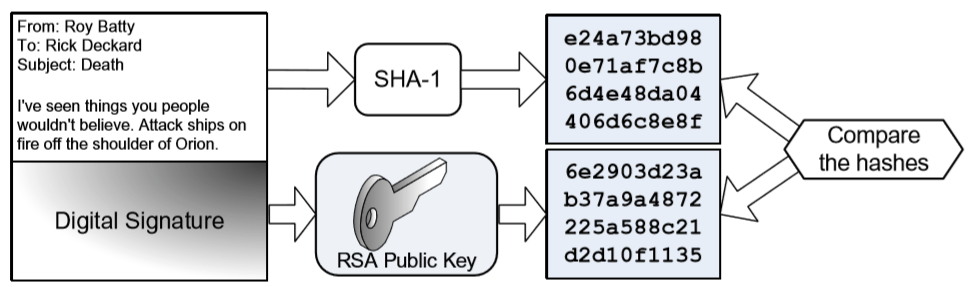
Answers in comments
Q1: (b) The sender encrypts the hash with a private key (and the recipient decrypts the hash with a public key)
Q2: (a) IaaS – Infrastructure as a Service (provides the entire virtualised OS, which the customer configures from OS up)
Q3. (c) Inference (attacker “infers” that the building is empty; deducing sensitive information from public information)
Q4. (b) Integrity
Q5. The hash starting with “e24a” in the top right.
LikeLike